
The hacker holds about $4.3 million in various crypto assets in their Ethereum wallet.
Cryptocurrency Financial News

The hacker holds about $4.3 million in various crypto assets in their Ethereum wallet.
A new rug pull alert sounded on Tuesday after crypto detective ZachXBT unveiled on-chain details of an alleged hack suffered by an NFT project last month. The project’s CTO announced that a response was in the works but ultimately vanished as criticism grew.
On-chain sleuth ZachXBT revealed the alleged misuse of funds by the CTO of NFT project Nuddies NFT. In a now-deleted post, its CTO Kyle explained that the project was “derugged from its previous founder” and built differently from other NFT projects.
A short investigation into how @kyledegods faked a hack and stole SOL from his project @NuddiesNFT before spending it on NFTs and lying to holders about how devastated he was about the incident.
On March 3, 2024 Kyle made a post in his Discord server claiming his wallets had… pic.twitter.com/4ne6dtVyA5
— ZachXBT (@zachxbt) April 2, 2024
According to the crypto detective, Kyle faked a hack that seemingly stole the project’s funds. On March 3, the alleged culprit posted on the Nuddies NFT Discord server, informing us of the hack.
The post affirmed that Kyle’s Mac was hacked despite “not clicking in any malicious link.” The CTO concluded that a “zombie process” was on his computer for an undetermined period.
This “mini-program” gave control of the computer to “the hacker.” Through the TeamViewer app the attacker gained access to the project and Kyle’s wallets. The post further explained that 90 SOL, approximately $17,000 at today’s price, were taken from the Nuddies NFT creator wallet.
Moreover, the hacker allegedly took control of Kyle’s Discord and stole 150 SOL, worth around $28,300, from his wallets. At the time, he claimed to be “mentally destroyed” by the loss of the project’s treasury money.
Nonetheless, the on-chain data compiled by ZachXBT tells a different story. Per the crypto detective’s post, the CTO allegedly lied to the holders and stole the 94 SOL, worth $12,000, when the incident occurred.
The post reveals that the funds were transferred during that day from the Nuddies Royalty Wallet to an exchange deposit at 8:20 UTC. The on-chain investigator claims that a destination transaction was found using time analysis. The transaction to one of Kyle’s wallets accounted for 3.42 ETH, around $11,700, at 8:21 UTC.
The ETH was seemingly used to buy two NFTs: DeGods 2921 and y00t 10991. The DeGod NFT was used as the CTO’s profile picture on X until yesterday.
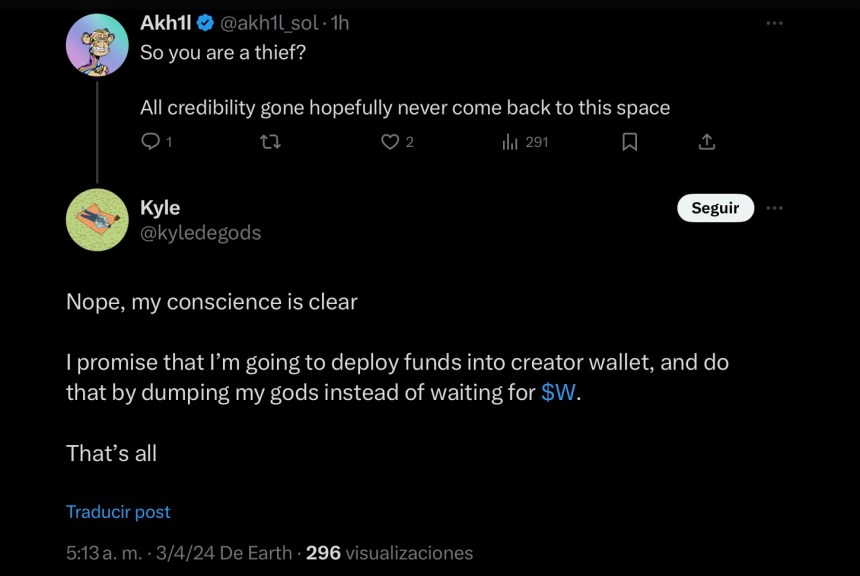
The accusations didn’t go unnoticed by the suspect, who posted on his X account that he was “preparing the answer” with a wink face emoji. After changing his profile picture, Kyle answered some users’ questions about his credibility, to which he replied that his “conscience is clear.”
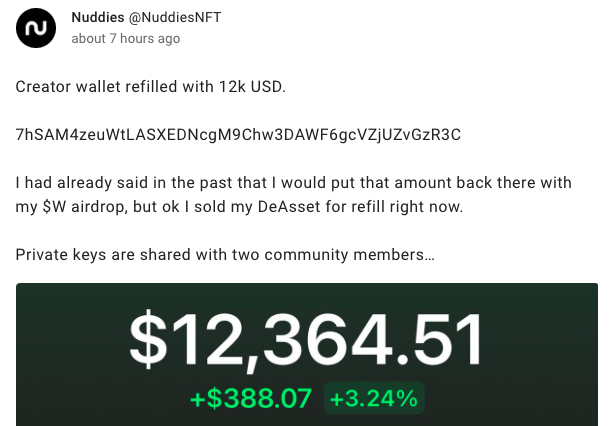
In the early hours of Wednesday, Nuddies NFT account shared a now-deleted post informing that the creator wallet was “refilled with 12k USD.” In the post, Kyle reassured that his previous claims of intending to refill the wallet were authentic.
The CTO also claimed he was “waiting for his $W airdrop” to fulfill his promise instead of selling his DeAsset. Additionally, he “stepped out” of the project after giving the access keys to two community members.
However, the story doesn’t end there. Kyle and Nuddies NFT’s account were deleted a couple of hours after the post. The Nuddies website seems not to be working, as reported by an X user.
The project’s future is unsure as one of the community members to whom Kyle gave the access keys was unaware of the situation. Juiceddd, an NFT artist, is one of the two people in charge of the project.
The artist explained that he was responsible for redrawing the entire Nuddies collection while adding “70+ new traits.” Moreover, Juiceddd stated that he “woke up this morning to being the owner of everything.” The artist is contemplating giving his perspective on the incident as he considers that it is generally the artist who “gets fucked” in these situations.
In the late hours of Tuesday, Trezor’s X account was compromised. The hacker used the hardware wallet company account to promote a fake crypto presale with a malicious link attached.
Members of the crypto community quickly realized the suspicious activity from the company and alerted other X users about the scam. Since then, Trezor’s team has regained control of the account.
In the now-deleted tweets, the hacker announced that Trezor was “willing to support the $SLERF Community.” Taking advantage of the ongoing efforts from crypto projects and exchanges to raise funds for the affected participants of the Slerf presale debacle.
Community alert: Trezor X/Twitter account is currently compromised pic.twitter.com/hNm2OUjEgE
— ZachXBT (@zachxbt) March 19, 2024
The unauthorized post offered the presale of a fake $TRZR token, which required interested users to send SOL to the hacker’s address. Additionally, Trezor supporters would receive a “separate bonus airdrop” if they went to a website linked in the post.
As it’s customary for phishing scams, the link would redirect to a wallet drainer that takes control of the person’s wallet after they try to “claim the airdrop tokens.”
The crypto community shared their thoughts on the hack. A user pointed out that the security breach was a “bad look” for the company as it focuses on crypto security. Others thanked the users who warned about the hack since it potentially saved them and others from falling for it.
It’s worth noting that many users have raised their concerns about the community’s reaction to the Slerf presale drama. They consider that raising funds for the participants affected sets a precedent of “bailing out” bad actors and will only “enable” similar behavior.
Moreover, scammers have been trying to prey on the community’s good faith to help potential victims and newcomers. As seen with the Trezor hack, the scammer seemingly tried to maximize its gains by utilizing the presale meta trend and the Slerf drama.
Usually, the recounting of crypto hacks ends with staggering figures being stolen, but for once, the tale is different. As reported by ZachXBT, the hacker managed to steal $8,100 from the unauthorized post, which includes the 25% drainer fee. As part of the loot, the hacker also received a “whooping 0.96 Solana,” as another user pointed out.
Many wondered if the small amount stolen was due to the community intelligently recognizing the scam or the hacker’s inability to perform a big heist. Whatever the case, this is a remarkable feat as the cold wallet company amasses over 200,000 followers that momentarily became potential victims.
— 赤 – 紅色的 (@Ikuma_On) March 20, 2024
Despite this small victory for the community, “It’s $8.1K more than 0,” as one user said. This raises the question of whether the hack was possible due to a lack of proper security measures or an inside job taking place.
No official explanation has been given yet. Nonetheless, Trezor acknowledged the hack in an X post earlier today.
Alert
We experienced a security incident on our X/Twitter account overnight, despite robust protections including a strong password and 2FA. We continue to investigate.
Please remain vigilant and remember, Trezor will NEVER request funds or assets be sent to any address.…
— Trezor (@Trezor) March 20, 2024
The company affirmed that the hack happened despite its “robust protections,” including two-factor authentication (2FA). At the time of writing, Trezor is continuing its investigation. The statement closed with a message for all users to “remain vigilant.”
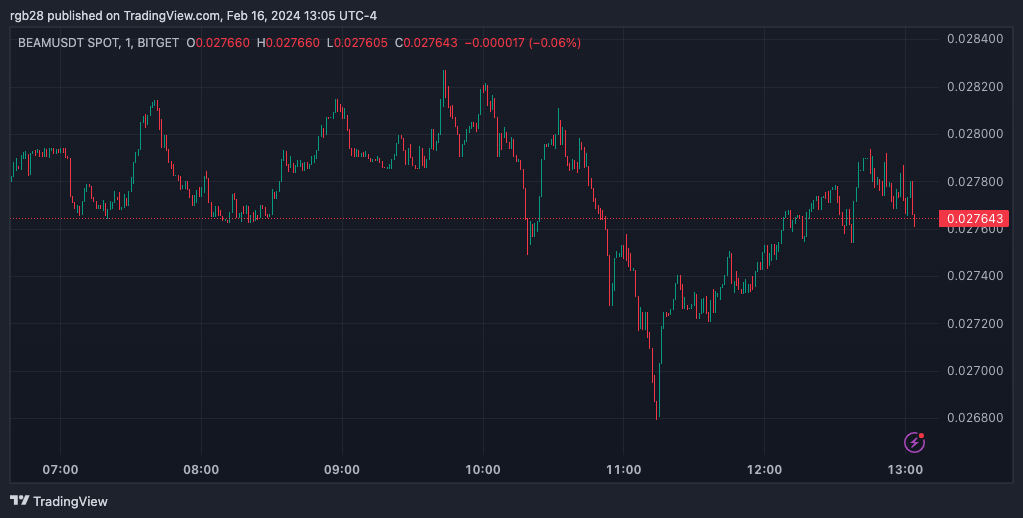
According to the blockchain analytics platform Lookonchain, a crypto trader suffered a phishing attack that swooped over 180 million BEAM tokens on Wednesday and affected the token’s price.
In an X (former Twitter) post, Lookonchain exposed a new crypto scam that had occurred on February 15. As the analytics platform detailed, the address 0x83664B8a83b9845Ac7b177DF86d0F5BF3b7739AD, under the name ‘Kirilm.eth’, suffered a phishing attack that led to the theft of millions of BEAM tokens.
kirilm.eth was phishing attacked and lost 180.25M $BEAM($5.14M) 13 hours ago.
The scammer quickly sold the 180.25M $BEAM for 1,629 $ETH($4.6M), which caused the price of $BEAM to drop by ~7%.https://t.co/x8epiNx4Qa pic.twitter.com/ytcfYib2Kg
— Lookonchain (@lookonchain) February 16, 2024
Users seemingly identified the victim as a crypto trader named Kirill Marinov. According to the information provided, the victim lost 180.25 million BEAM tokens, worth approximately $5.14 million, to an account labeled as ‘Fake_Phishing291038.’
Shortly after the theft, the scammer’s address liquidated the total amount of stolen BEAM tokens, exchanging them for 1,629 ETH worth approximately $4.6 million.
According to Web3 anti-scam platform Scam Sniffer, the victim signed an ‘increase allowance’ transaction that gave the scammer access to the tokens. Additionally, the. X post detailed that the token spender is a Safe Wallet address.
However, this writing has not revealed further details about the victim, the exact tactics used by the scammer, and their identity.
Phishing scams are among the most popular tactics for crypto-related crimes. Scammers exploit inexperienced investors’ naivety and oversights from more experienced traders to gain access to the funds.
The scamming tactics involve a variety of ways to trick the victims into revealing their private keys or login information to grant access to the victim’s wallets. Due to this, experts urge all crypto investors to stay alert and take the necessary measures to keep their assets safe.
The BEAM token serves as the native crypto asset for the Beam network. After the heist and subsequent exchange to ETH, the token’s price dropped, falling from the $0.030 price level to the $0.028 range.
Beam Network is a gaming network powered by the Merit Circle DAO. The ecosystem brings developers and gamers together to develop the gaming industry further. According to the Beam team, “At its core, Beam aspires to create harmony between gamers and developers.
It’s not just about gaming; it’s about ownership, empowerment, and a global community. Every feature and tool is a step towards this visionary future.”
At writing time, the token trades at $0.027, representing a 2.4% drop in the last hour and a 9.3% decrease from its trading price in the previous 24 hours. According to CoinMarketCap data, the token’s daily trading volume saw a 25.7% decrease in the last 24 hours, sitting at the #104 spot on this metric with $61.4 million.
Despite the negative price reaction following the scam, the BEAM price still registered a 32.9% increase in the last 7 days. Similarly, BEAM’s trust score in the spot markets remains untouched, per CoinGecko Data.
Hardware wallet manufacturer Ledger has responded to a recent security breach resulting in the theft of $600,000 worth of user assets.
The company has pledged to enhance its security protocols by eliminating Blind Signing, a process where transactions are displayed in code rather than plain language, by June 2024.
In a statement, Ledger emphasized its focus on addressing the recent security incident and preventing similar occurrences in the future.
The company acknowledged the approximately $600,000 in assets that were impacted by the ConnectKit attack, particularly affecting users blind signing on Ethereum Virtual Machine (EVM) decentralized applications (dApps).
Furthermore, Ledger pledged to make sure affected victims are fully compensated, including non-Ledger customers, with CEO & Chairman Pascal Gauthier personally overseeing the restitution process.
According to the statement, Ledger has already initiated contact with affected users and is actively working with them to resolve their specific cases.
In addition, by June 2024, blind signing will no longer be supported on Ledger devices, contributing to a “new standard of user protection” and advocating for “Clear Signing,” which refers to a process that allows users to verify transactions on their Ledger devices before signing them across dApps.
On this matter, Ledger’s CEO Pascal Gauthier stated:
My personal commitment: Ledger will dedicate as much internal and external resources as possible to help the affected individuals recover their assets.
According to an incident report released by the hardware wallet manufacturer, the attack exploited the Ledger Connect Kit, injecting malicious code into dApps utilizing the kit.
This malicious code redirected assets to the attacker’s wallets, tricking EVM dApp users into “unknowingly signing transactions” that drained their wallets.
Ledger addressed the attack by deploying a genuine fix for the Connect Kit within 40 minutes of detection. The compromised code remained accessible for a limited time due to the nature of content delivery networks (CDNs) and caching mechanisms.
Ledger acknowledged the risks faced by the entire industry in safeguarding users and emphasized the need to continually raise the bar for security in dApps.
The company plans to strengthen its access controls, conduct audits of internal and external tools, reinforce code signing, and improve infrastructure monitoring and alerting systems.
Additionally, Ledger will educate users on the importance of Clear Signing and the potential risks associated with blind signing transactions without a secure display.
Notably, with Clear Signing, users are presented with a clear and readable representation of the transaction details, enabling them to review and validate the transaction before providing their signature.
This added layer of transparency and verification helps users mitigate the risks associated with front-end attacks or malicious code injected into decentralized applications
Featured image from Shutterstock, chart from TradingView.com
Aurory (AURY), a blockchain-based tactical Japanese role-playing game built on Solana (SOL), recently experienced a significant liquidity loss in its Camelot’s AURY-USDC pool.
The incident occurred due to a hack on the SyncSpace bridge, which resulted in the unauthorized withdrawal and subsequent market sale of approximately 600,000 AURY tokens on the Arbitrum (ARB) network.
In an official statement released on December 17, Aurory’s team disclosed the details of the incident. The team detected unusual activity on their marketplace and promptly initiated an investigation, which revealed that a malicious actor had exploited the marketplace’s buy endpoint.
This exploit allowed the attacker to inflate their AURY balance in SyncSpace, enabling them to withdraw around 600,000 tokens to the Arbitrum network. The attacker then liquidated the stolen amount by selling it in the market.
To protect user funds, SyncSpace was promptly disabled for maintenance, temporarily suspending deposits and withdrawals. Importantly, the statement assured that no user funds or non-fungible tokens (NFTs) were lost or at risk during the incident.
The AURY tokens originated from a team wallet, facilitating withdrawals for accounts not previously deposited AURY.
The Aurory statement emphasized that the exploit is no longer ongoing, as SyncSpace remains offline for maintenance. As a result, there is currently no risk of further exploits. Additionally, it was confirmed that the attacker has exhausted their AURY supply and no longer possesses any tokens to sell.
Moreover, SyncSpace will investigate further to determine how the exploit went undetected despite the previous expert audit.
The team also plans to release a comprehensive post-mortem report once the necessary fixes have been implemented and the investigation concludes. They expect SyncSpace to be back online in the coming days.
Since October 30, the price of Aurory’s token, AURY, has experienced a significant upward trend, culminating in a yearly high of $1.9008 on December 12. However, following the recent exploit, the price of AURY has retraced to $1.0868, marking a decline of 23.5% over the past 24 hours and 36.5% over the past seven days.
Despite this setback, AURY still boasts substantial gains of 74% and 70% over the 30-day and one-year periods, respectively.
The market now awaits to see whether the token’s support lines at $0.9681 and $0.9086 will be able to halt the potential continuation of the price drop or if they will succumb to the prevailing downtrend, putting a significant portion of its 2023 gains at risk.
Featured image from Shutterstock, chart from TradingView.com
Kronos Research, a Taipei-based market maker, trading firm, and venture capital fund, witnessed the withdrawal of significant amounts of crypto assets due to a breach of its security system.
On Sunday, November 19, Kronos Research disclosed – via a post on X (formerly Twitter) – a security incident that involved unauthorized access to its API keys. Consequently, the company lost a significant amount of crypto funds and has halted all trading operations in a bid to launch a full investigation into the incident.
In the interest of transparencyAround 4 hours ago, we experienced unauthorized access of some of our API keys. We paused all trading while we conduct an investigation. Potential losses are not a significant portion of our equity and we aim to resume trading as soon as possible.
— Kronos Research
(@ResearchKronos) November 18, 2023
A map of funds outflow by on-chain sleuth ZachXBT summed Kronos’ losses to over $25 million in Ether. In a follow-up post on X, the company also confirmed that the losses are about $26 million in crypto assets.
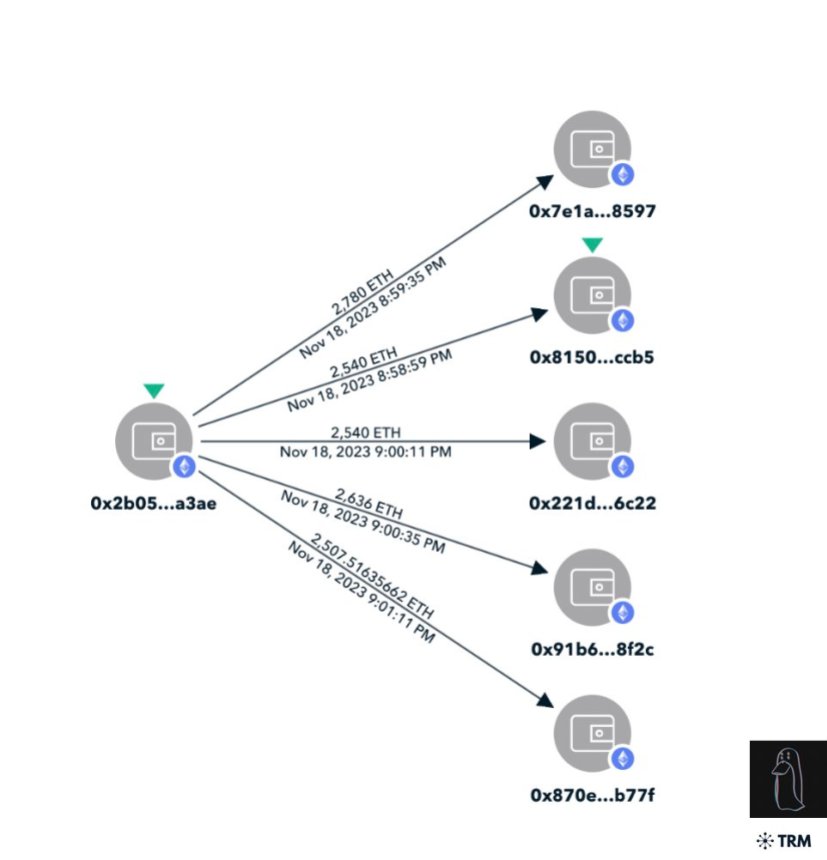
In its initial announcement, Kronos revealed that the potential losses are not a significant portion of its equity. Meanwhile, the trading firm said in its latest update that all losses will be covered internally, and no partners will be affected.
Although Kronos has yet to provide an update on its resumption process, the company did say that it aims to resume trading as soon as possible.
This $26 million attack on Kronos Research represents the third most significant crypto theft in November 2023. Before this latest incident, data from blockchain security firm Certik revealed that about $173 million had been lost to crypto attacks in November, with Poloniex’s $113 million hack being the most notable yet.
Interestingly, Kronos is not the only one affected by this security incident, as WOO X is another cryptocurrency entity that has had to pause its operations momentarily. WOO X is an exchange on which Kronos functions as the market maker for its spot and perpetual futures markets.
In an address on the X platform, WOO X acknowledged Kronos’ security situation and announced a temporary pause on all trading to protect users’ positions from a lack of liquidity. The exchange, however, emphasized that all customer funds are safe.
As of this writing, WOO X has resumed trading in both the spot and perpetual futures markets. Meanwhile, the exchange claims that clients can now make withdrawals for all assets.
Nevertheless, the trading platform has faced some backlash from the online crypto community, with some people pointing to its unclear relationship with Kronos.
Crypto exchange platform Poloniex was attacked by a bad actor, losing over $60 million of its customer’s funds. The Justin Sun led the exchange and launched an investigation, which remains ongoing, to determine the identity of the attackers.
The crypto analytics platform Nansen data indicates that over $68 million in tokens left Poloniex over the past day. The image below shows that the attacker stole assets in ETH, BADGER, REN, OKB, NEXO, and 170 other tokens.
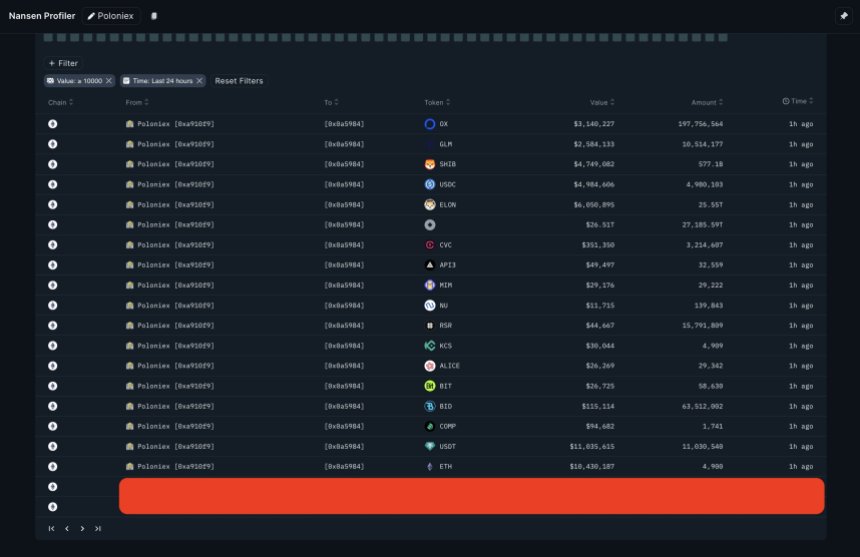
Nansen also confirmed that the biggest losses were suffered in top assets, Ethereum and USDT, with around $11 million each. Other tokens such as ELON, USDC, SHIB, and GLM saw inferior losses but still in the millions of dollars.
A few hours ago, as mentioned, the exchange launched an investigation and Justin assured its users that the platform keeps a “healthy financial position.” In that sense, Sun, also the founder of blockchain TRON, claimed that users will be reimbursed for their losses.
The platform is currently exploring a partnership with other crypto exchanges to recover the fund. Sun stated:
We are offering a 5% white hat bounty to the Poloniex hacker. Please return the funds to the following ETH/TRX/BTC wallets. We will give you 7 days to consider this offer before we engage law enforcement.
In the crypto community, some users praised these efforts to recover the fund and encouraged the attacker or attackers to take the bounty for “pointing out vulnerabilities” in the platform’s security. However, other users were critical of the measure. One community member stated:
(…) a white hat doesn’t steal funds and then ask for a bounty, whatever you’re promising, law enforcement will be involved. It’s like saying you can beat someone to death but if you take them to the hospital you’ll be safe (…).
It remains to be seen if the attacker will accept the offer. In the crypto space, many cyberattacks have been conducted by state-sponsored hacker groups, such as the infamous Lazarus Group, allegedly working for the North Korean Government.
According to a report from our sister website, Bitcoinist, this group stole billions of dollars from the nascent industry in the past two years. The terrorist group is allegedly a key component of the country’s nuclear program. Jason Bartlett, a researcher at the Center for a New American Security (CNAS), said:
Cryptocurrency offers Pyongyang a new kind of currency that is substantially less regulated and understood by national governments, financial institutions, and international organizations.
However, cryptocurrencies also operate as an important tool for law enforcement agencies to track down and cut funding for rogue entities. Due to blockchain technology’s transparency, some criminals stay clear of digital assets and crypto exchanges.
As of this writing, Ethereum (ETH) trades at $2,077 with a 7% profit in the last 24 hours.
Cover image from Unsplash, chart from Tradingview
In a chilling development on Halloween Day, the crypto community was hit with disturbing news as PeckShield, a renowned blockchain security company, revealed a series of rug pulls over the past few hours.
Rug pulls, a form of cryptocurrency scam, involve sudden and deliberate value drops in specific tokens, accompanied by the perpetrators swapping the native tokens for Ethereum (ETH). The meme coins affected by the rug pulls were identified as MEME, MEMEPAD, and TITANX.
According to PeckShield’s X (formerly Twitter) post, the MEME token on the Ethereum blockchain experienced a jaw-dropping 100% drop in value. The address 0xBd72…5871 was responsible for swapping a staggering 4,854,740,126,240,000 MEME tokens for approximately 43.68 ETH.
It is important to note that the rug pull token shared the same name as the legitimate MEME token, adding to the confusion.
Similarly, the MEMEPAD token on Ethereum suffered an identical 100% value drop. The address 0xBd72…5871 conducted a swap of 4,854,740,126,240,000 MEMEPAD tokens for around 44.84 ETH.
Once again, the fraudulent crypto rug pull shared the same name as the genuine MEMEPAD token, compounding the deceitful nature of the scam.
Additionally, the TITANX token launched two days ago, October 28, on Ethereum experienced a staggering 100% value decline.
The address 0xBd72…5871 executed a swap of 4,854,740,126,240,000 TITANX tokens for approximately 46 ETH. Mirroring the previous instances, the rug pull token masqueraded under the same name as the legitimate TITANX crypto token.
In alarming events, the Fantom (FTM) Foundation finds itself entangled in a harrowing tale of fund drains and swift token swaps. PeckShield has reported two significant incidents involving the Fantom Foundation’s finances, leaving the organization with substantial losses.
The first incident occurred on October 17, 2023, when wallets associated with the Fantom Foundation were drained of approximately $7 million worth of cryptocurrencies, equivalent to around 4,500 ETH.
Additionally, on October 26, the Fantom Foundation faced another devastating event. An unidentified entity, the “Fantom Foundation Drainer,” executed a bold move by swapping a staggering 8,087,377.97 DAI for 4,560.52 ETH.
The gravity of the situation intensified when the Fantom Foundation Drainer swiftly executed another swap on October 30, converting the 4,560.52 ETH back into approximately 8.3 million DAI within a mere 30 minutes.
The Fantom Foundation is now faced with the daunting task of investigating the breaches, identifying the culprits, and fortifying its security infrastructure to prevent future incidents.
Despite recent developments, the native token of the Fantom protocol, FTM, is trading at $0.2388, reflecting a 1% increase in the past 24 hours.
Notably, the token has experienced a substantial surge across various time frames. Presently, it has maintained an upward trend, with gains of over 6% and 30% in the seven-day and fourteen-day periods, respectively.
Over the year-to-date period, the token has recorded a 5% increase. These figures indicate the token’s positive performance and growth trajectory.
Featured image from Shutterstock, chart from TradingView.com

The exploiter of the Web3 social media platform agreed to keep a 10% bounty in exchange for returning the remainder of the stolen funds.
Reports from South Korea-based Yonhap News Agency have revealed that Upbit, one of the largest crypto exchanges in South Korea experienced over 159,000 hacking attempts in the first half of 2023 alone.
According to the data from Upbit’s parent company Dunamu shared with the local news agency, the hacking attempts of the first half of 2023 indicate a 117% increase compared to the first half of 2022, and a 1,800% increase in hacking attempts compared to the second half of 2020.
The crypto exchange recorded 8,356 hack attempts in the second half of 2020, 34,687 in the first half of 2021, 63,912 in the second half of 2021, 73,249 in the first half of 2022, and 73,249 in the second half of 2022.
These hack attempts have increased over the years after the crypto exchange suffered a hack of 58 billion won ($50 million) in 2019. The exchange has since successfully fortified its security measures to prevent these hacks, and the exchange has not experienced any exploit since 2019.
“After the hacking incident in 2019, we took various measures to prevent a recurrence, such as distributing hot wallets and operating them, and to date, not a single cyber breach has occurred,” a Dunamu Official stated.
Some of these measures included an increased percentage of money retained in cold wallets by 70%. Hot wallets, which keep keys online and are more susceptible to breaches, are thought to be less secure than cold wallets, which store private keys offline.
This is because the majority of known cryptocurrency exchange hacking instances have occurred in hot wallets, especially the crypto hacks that occurred in September. One such example is Hong Kong-based CoinEx which suffered a $70 million hack in September 2023, and Mixin Network which suffered a $200 million hack, among others.
Due to the significant increase in cryptocurrency hack attempts in South Korea, the country’s Representative Park Seong-jung has called upon the South Korean government to take considerable measures to handle the issue.
“The Ministry of Science and Technology must conduct large-scale whitewashing mock tests and investigate information security conditions in preparation for cyber attacks against virtual asset exchanges where hacking attempts are frequent,” Representative Park said.
Upbit recently experienced an issue in late September 2023, where the crypto exchange was unable to identify a fake token, “ClaimAPTGift.com, present in 400,000 Aptos wallets. This led to the suspension of Aptos token services.
September 2023, was a nightmare for certain crypto exchanges as about $332 million in crypto assets were stolen from certain crypto exchanges in September alone.
Blockchain security firm Certik took to their official X handle in late September to share the compilation of the crypto hacks that occurred in the month alone and how much was stolen from these incidents.
The stolen funds accounted for exploits, exit scams, and flash attacks. However, exploits accounted for the most, with over 98% ($329.8 million) of the total amount stolen in that month, while exit scams and flash attacks accounted for the rest.
As the crypto market continues to attract substantial investments, it has also witnessed a surge in scams and fraudulent activities. Regulatory institutions worldwide, spearheaded by the United States, seem to intensify their efforts to combat cyber threats, hacks, and frauds that affect the industry.
However, the nascent sector is far from the only one suffering from increasing cyber threats. Since 2020, these attacks have been common both within the crypto space and outside.
In line with this, the Federal Bureau of Investigation (FBI) identified a new threat dubbed “The Phantom Menace.” The FBI issued a warning on September 29, alerting the public about the escalating “Phantom Hacker” scams, particularly affecting senior citizens.
The FBI’s statement revealed that the “Phantom Hacker” scam is an evolution of traditional tech support scams, employing imposter tech support, fraudulent exchange account support, and government personas to gain victims’ trust. This multi-layered approach helps scammers identify lucrative accounts to target.
From January to June 2023, the FBI Internet Crime Complaint Center (IC3) received over 19,000 complaints about tech support and crypto scams, resulting in estimated losses exceeding $542 million. Losses have already surpassed 2022 figures by 40% as of August 2023.
The Scam Phases:
Once victims are connected, scammers manipulate them into downloading software that grants remote access to their computers. By fabricating a fictitious virus scan, scammers deceive victims into believing their computers have been compromised or are at risk.
Subsequently, they coax victims into opening their financial accounts, allowing scammers to identify the most lucrative targets.
The scammers falsely inform victims that foreign hackers have compromised their computers and accounts. To ensure the safety of victims’ funds, they instruct victims to transfer their money to a purportedly “secure” third-party account, often claiming an affiliation with recognized entities like the Federal Reserve or other US government agencies.
These transfers typically involve wire transfers, cash, or even cryptocurrencies, with the funds predominantly sent overseas. Scammers coerce victims into maintaining secrecy regarding the true purpose of these transfers.
In contrast with the alarming rise of “Phantom Hacker” scams, a Chainalysis report indicates an overall decline in cryptocurrency-related crime in 2023. Cumulative daily inflows to known illicit entities have decreased by 65% compared to the same period in 2022.
Notably, scams have experienced the most significant decline, with scammers generating nearly $3.3 billion less revenue in 2023 than in 2022. However, the report highlights a concerning trend: ransomware attacks.
Ransomware attackers extorted $175.8 million more by June 2023 than during the same period in 2022, suggesting a reversal from the downward trend observed in 2022.
While overall crypto-related crime has declined, the resurgence of ransomware attacks poses a significant menace and could spill over to the nascent sector. While the number declines, the amount stolen in the crypto space urging users to remain cautious in the face of new threats.
Featured image from Shutterstock, chart from TradingView.com

Mark Cuban confirmed that he was hacked, but doesn’t appear to know exactly how it happened as of yet.

Mark Cuban confirmed that he was hacked, but doesn’t appear to know exactly how it happened as of yet.
On Tuesday, September 12, centralized crypto exchange CoinEx became the latest victim of a hack. At the time of the reports, over $27 million in crypto had already been carted away by the attackers. However, almost 24 hours later, the reports rolling in suggest that the exchange may have lost double the amounts that were originally reported.
The initial reports for the CoinEx hack showed that the attackers were able to move around $27.8 million from the exchange. But as investigators dig further into the attack, the losses have come up to around $55.5 million in crypto lost so far.
According to a breakdown posted by Wu Blockchain, a platform run by Chinese reported Colin Wu, the losses extended into lesser-known tokens as well. The majority of the losses were from assets such as Ethereum, Bitcoin, and XRP, with assets on the BSC, Polygon, and Kadena blockchain also running into the millions.
The ETH amount drained alone came out to over $18 million, as shown in the breakdown, while over $11 million was stolen in Tron’s TRX token. Other notable transactions include $6 million in XRP, over $6.2 million in BNB, $5.9 million in Bitcoin (BTC), $2.5 million in Solana’s SOL, $1.7 million in Dagger’s XDAG, and $1.12 million in Kadena’s KDA. There was also a little over $440,000 stolen in Bitcoin Cash’s BCH.
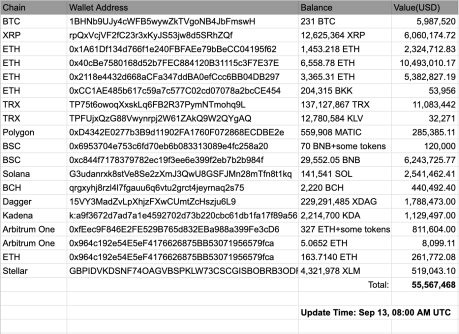
At the time of writing, a total of $55,567,468 has been confirmed stolen from the hacking incident from the exchange. The crypto stolen from the crypto exchange was sent to 19 wallet addresses spanning 12 blockchains.
In the aftermath of what has been the largest centralized crypto exchange hack in 2023, CoinEx has promised to compensate all of its affected users in full. The statement which came a couple of hours after the incident was identified told users:
You have our solemn promise that a detailed timeline and comprehensive report about this incident will be shared with the community as swiftly as possible.
For now, users are unable to transact on the crypto exchange as deposits and withdrawals remain unavailable. However, the exchange said in its statement that this was only a temporary measure and that these activities “will resume after a thorough review.”
Over the day, the exchange has also taken to posting the wallet addresses it has identified to be linked to the attack. This is being done in an effort to raise awareness about their activities. “We urge affected projects and fellow industry colleagues to assist in flagging and freezing these questionable addresses,” CoinEx said in an X post.
On September 11, the hacker first transferred 520,000 MATIC tokens, worth over $266,000, which were bridged to the Avalanche blockchain. Some hours later, 300 BNB tokens valued at approximately $61,500 were sent to an externally owned address labeled “0x695…”.
Before these recent transfers, the hacker had bridged $4.5 million to different Bitcoin blockchain addresses. This was reported by the blockchain security company Arkham on September 7. The total amount transferred, now at $4.8 million, only constitutes 1.2% of the total $41 million stolen by the hackers.
The Stake hackers exploited the platform by gaining access to the private keys of the platform’s Binance Smart Chain and Ethereum hot wallets.
According to the United States Federal Bureau of Investigation (FBI), the Lazarus Group from North Korea – known for its involvement in various cybercrimes, including hacking and cryptocurrency-related attacks, might be behind this exploit.
The recent hack of $41 million from Stake has contributed to the cumulative losses from cryptocurrency hacks and scams in 2023. As a result of this incident, the total losses in the cryptocurrency industry have now surpassed the $1 billion mark.
Before the Stake attack, CertiK had reported the total losses to be approximately $997 million at the end of August. But for August alone, CertiK reported that exit scams resulted in approximately $26 million in losses. Flash loan attacks accounted for $6.4 million, and exploits caused losses of $13.5 million.
The cybersecurity firm verified that these combined losses exceeded $45 million for the past month. However, with several attacks occurring in the past two weeks, the overall figure has now crossed the $1 billion threshold.
For instance, a prominent cryptocurrency investor lost $24 million of staked Ether (ETH) in a phishing attack on September 6. Additionally, Vitalik Buterin’s X (formerly Twitter) account was compromised on September 9, and the hacker used it to trick several individuals into participating in a nonfungible token scam, resulting in a total loss of $691,000.
Considering these incidents, in addition to CertiK’s previous estimate from August, the total losses due to cryptocurrency-related incidents would now exceed at least $1.04 billion.
Other recent incidents include a withdrawal involving Pepe coin (PEPE), resulting in a loss of $13.2 million for investors. Also, a security vulnerability was exposed on the Balancer platform, resulting in damages totaling $2.1 million.
In a concerning development, popular crypto exchange CoinEx is believed to have fallen victim to a suspected hack, resulting in significant losses from its Ethereum (ETH), TRON (TRX), and Polygon (MATIC) hot wallets. The incident, which unfolded on Tuesday, has sparked an ongoing investigation into the security breach.
According to reports by Colin Wu, a prominent cryptocurrency journalist, CoinEx reportedly lost a staggering 4,946 ETH and 354,762 TRX as part of the ongoing drain from the exchange’s wallets.
The total value of the funds lost surpasses $27.8 million, adding to the growing list of high-profile cryptocurrency exchange breaches. In his latest update, Colin Wu stated:
CoinEX is moving the affected hot wallet assets to the cold wallet address 0xf54…7E5d. CoinEX wallets currently hold $97.83 million in assets, of which $89 million are stored in the cold wallet address 0xf54…7E5d, mainly ETH worth $51.7 million and USDT $18.23 million.
What’s more, In a concerning revelation, Julio Moreno, the Head of Research at CryptoQuant, has shed light on the peculiar behavior surrounding CoinEx’s Ethereum reserves.
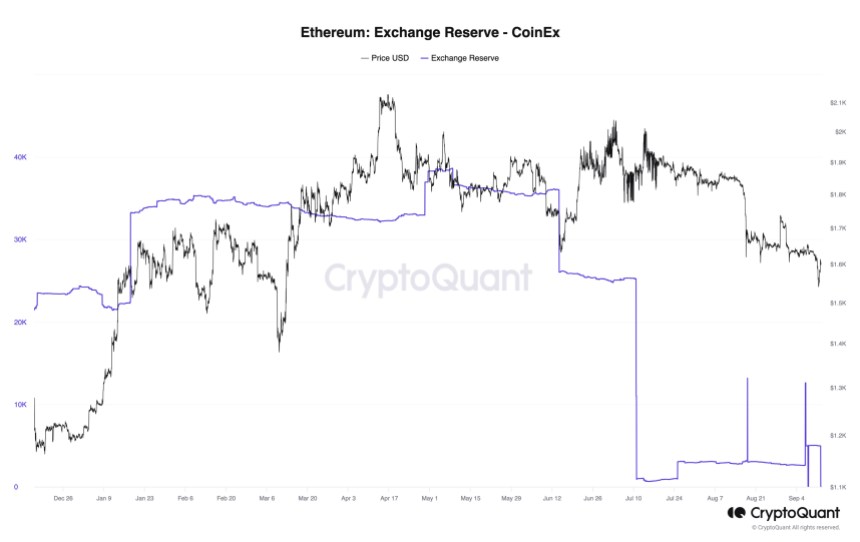
The exchange has experienced a staggering depletion of its ETH holdings, with almost 5,000 ETH mysteriously vanishing within a single hour and a total loss of approximately 40,000 ETH since May. As a result, CoinEx’s ETH reserves now stand at virtually zero.
CoinEx, however, has remained silent on the matter, refraining from issuing an official statement regarding the suspected hack.
The depletion of CoinEx’s ETH reserves indicates a potentially grave situation, as it suggests a significant outflow of funds from the exchange. Such a rapid decline in ETH holdings may have severe implications for CoinEx’s liquidity and ability to meet customer withdrawal demands.
CoinEx’s stakeholders and the wider cryptocurrency community will closely watch how the exchange responds to these developments. Complemented by transparent communication, swift and decisive action will be vital in navigating this challenging situation and working towards a resolution.
Featured image from iStock, chart from TradingView.com
In a disheartening turn of events, the decentralized finance (DeFi) protocol Balancer (BAL) confirmed a hack just days after warning about a critical vulnerability impacting multiple Pools. The attack, which took place on August 27, resulted in a loss of nearly $1 million for Balancer.
Previously, on August 22, NewsBTC reported that Balancer had discovered a critical vulnerability affecting its protocol. However, despite efforts to mitigate the risks and caution users, Balancer could not pause the affected pools. In response, the protocol urged users to withdraw from the impacted liquidity pools to prevent further exploits.
On Sunday, Balancer took to X (formerly known as Twitter) to acknowledge the existence of an exploit related to the previously disclosed vulnerability. While mitigation measures were implemented to reduce risks, they were insufficient to halt the affected pools.
Consequently, users were advised to withdraw their funds from the vulnerable liquidity pools to safeguard their investments.
Meir Dolev, a Web3 security expert, shed light on the situation, revealing that the attacker was persistently carrying out their operation. Approximately $900,000 was affected, with over $600,000 already transferred to the address 0xB23711b9D92C0f1c7b211c4E2DC69791c2df38c1.
On the same note, Blockchain security firm Beosin further divulged that the hack was executed through multiple flash loan attacks. Flash loans, a feature enabling users to borrow funds without collateral, have been increasingly utilized as tools for exploitation in the DeFi space.
The Balancer exploit underscores the ongoing challenges DeFi platforms face in ensuring user funds’ safety. As the industry continues to innovate and attract significant capital, securing protocols and addressing vulnerabilities must remain a top priority.
In the aftermath of the recent exploit that targeted Balancer, the project’s native token, BAL, has experienced significant market repercussions.
The exploit, which resulted in a loss of approximately $1 million, has had a noticeable impact on BAL’s price and various key metrics, reflecting the challenges faced by the platform, according to Token Terminal data.
As a consequence, BAL’s price has witnessed considerable volatility. Over the past 30 days, the token has experienced a sharp decline of 20.81%, as seen in the chart below.
This downward trend is further highlighted by the token’s performance over a longer period of 180 days, during which it has plummeted by 51.69%, underscoring the impact of the exploit on investor sentiment and market confidence in BAL.
Furthermore, BAL’s all-time high (ATH) stands at $74.45, serving as a reminder of the token’s previous price peak. However, the all-time low (ATL) of $3.36 reveals the extent of the token’s decline following the exploit.
The exploit’s aftermath has also affected Balancer’s market capitalization metrics. The circulating market cap, representing the value of BAL tokens in circulation, currently stands at $150.06 million. However, this metric has suffered a notable decline of 22.60%, indicating a decrease in token valuation and investor confidence.
Another critical metric the exploit impacts is Balancer’s total value locked (TVL). TVL represents the amount of capital locked within the protocol.
In the aftermath of the exploit, Balancer’s TVL has declined by 33.86%, signaling a shift in investor sentiment and potential reallocation of funds to more secure platforms.
Featured image from iStock, chart from TradingView.com
In a new report, Estonia’s preeminent crypto payment and personal wallet provider, CoinsPaid, has revealed the intricate workings of a hacking incident that led to a colossal loss of $37 million.
This audacious breach was reportedly the culmination of a six-month saga marked by calculated maneuvers and sophisticated tactics, orchestrated by none other than the notorious Lazarus Group.
Collaborating with Match Systems, CoinsPaid embarked on a comprehensive inquiry, unearthing the modus operandi of the hacking group and exposing the subsequent laundering of pilfered assets in a post.
The ploy, characterized by an extraordinary level of meticulousness, spanned half a year, revealing the calculated and relentless nature of the hack. Employing a blend of social engineering and technical strategies, the hackers engaged in a series of Distributed Denial-of-Service and brute-force attacks.
Their calculated approach culminated in a July 22 breach with the manipulation of a CoinsPaid employee, ensnaring them through a falsified job proposition. The ordeal began innocently enough, as a CoinsPaid employee embarked on a video interview for what appeared to be an enticing career prospect, facilitated via LinkedIn.
Little did they know that the seemingly innocuous task of downloading a technical assessment was part of an elaborate ruse orchestrated by the hackers. This single act granted the hackers access to CoinsPaid’s systems, allowing them to exploit software vulnerabilities and authorize unauthorized withdrawals from the company’s hot wallets.
The hacker executed a swift sequence of unauthorized withdrawals, swiftly depleting the company’s coffers in less than an hour of operation. In total, CoinsPaid lost $37.3 million in the attack.
CoinsPaid’s exhaustive post-mortem report reveals invaluable lessons extracted from the breach. The report highlights the importance of training employees to identify social engineering tactics, including job offers that might be a ploy to gain access to internal systems.
The report also explains the adoption of principles like the Separation of Duties and Least Privilege, advocating for the implementation of robust monitoring and alert systems to detect suspicious activities.
Following the report, CoinsPaid will be hosting a roundtable discussion involving blockchain-based entities, aiming to collectively address the escalating threat posed by hacking incidents.
In the wake of the exploit, the payments platform assured customers that none of their funds were affected. The company also resumed all activities less than a week after the hack took place.
The Lazarus Group is believed to have stolen over $3.8 billion in digital assets from crypto exchanges and decentralized finance (DeFi) services since it became active.

The hacker managed to steal $794,000 worth of crypto from an exchange via a SIM swap attack on an exec, but ultimately he didn’t cover his tracks well.