
Binance’s new algorithm has already helped detect over 13.4 million spoofed blockchain addresses on BNB and over 1.68 million on Ethereum.
Cryptocurrency Financial News

Binance’s new algorithm has already helped detect over 13.4 million spoofed blockchain addresses on BNB and over 1.68 million on Ethereum.
A week ago, a crypto whale fell victim to a scam that resulted in the loss of over $71 million. In the following days, the scammer moved the funds to veil them. But in a shocking turn of events, they returned the funds to the victim.
On May 3, whale 0x1E22…8FD5 lost 1,155 Wrapped Bitcoin (WBTC), worth around $71.31 million, after falling victim to an address poisoning scam. This scam, also known as address spoofing, consists of trying to trick users into sending funds to fraudulent lookalike accounts.
#PeckShieldAlert #Phishing A whale 0x1E22…8FD5 lost ~1,155 $WBTC (worth ~$71 million) after falling victim to address poisoning.The phisher has swapped the stolen $WBTC for ~23K $ETH & transferred them out pic.twitter.com/dr7eTYQkAX
— PeckShieldAlert (@PeckShieldAlert) May 3, 2024
The “vanity addresses” are custom-made with specific characters that look like the intended recipient’s address. Scammers send transactions of no value, hoping the similarity between the addresses will fool the user under attack.
If successful, victims copy the fraudulent address from the previous transactions and accidentally send their assets to the scammers instead.
PeckShieldAlert reported that the phisher immediately swapped the stolen WBTC for 23,000 Ether (ETH) before transferring them to a different address. Throughout the following days, the scammer laundered the funds. Sending them to ten different addresses before distributing the tokens through over 100 other addresses.
This development painted a looming picture for the crypto whale. At this point, the funds appeared to be unrecoverable. One user called the massive number of transfers a “crypto musical chairs” game.
Others justified the scammer, claiming he had not stolen the funds, as “he just received them.” This stance disregards the transaction’s nature. The transfer occurs under the belief that funds are safely being transferred to the intended account and not a lookalike.
Moreover, the lookalike address is in the victim’s transaction history, clearly intended to deceive the user into receiving funds not meant for them.
In a shocking turn of events, the scammer sent 51 ETH, worth around $153,000, back to the victim on Thursday. Alongside the funds, the phisher sent a message asking to contact the whale, seemingly looking to negotiate.
The reasons behind the sudden change of heart remain a mystery to the community. Many are jokingly theorizing why the scammer returned the funds. One X user playfully suggested that the phisher feared being investigated by crypto sleuth ZachXBT.
Others claimed that “even the scammer doesn’t want ETH,” referencing the criticism the second-largest cryptocurrency has faced after its performance during this cycle.
In the early hours of Friday, PeckShieldAlert revealed that 2,683.7 ETH, worth about $8 million, had already been transferred to the whale from nearly 50 different addresses. A couple of hours later, an update showcased that around 50% of the total funds had been returned, accounting for 11,446.87 ETH, or $34.7 million.
Retrieving all the assets might take time due to the large number of addresses holding the funds. At the time of writing, over $45 million worth of ETH has already been returned, and the transactions continue.


Stolen crypto from a $71 million wallet impersonation scam is on the move after six days of dormancy.
The Solana memecoin frenzy has made many investors score a home run or be out of the game this cycle. Traders are looking for new projects that could be the next hit while the market enters a new re-accumulation phase.
Memecoins have been the narrative of this bull cycle. As a result, those who wanted to make big profits mainly invested in newly launched projects. While some have made millions by trading the week’s top gainers, others have lost significant amounts trying to climb the ladder.
Solana-based memecoins have been the most popular, with some, like dogwifhat (WIF) and cat in a dog’s world (MEW), leading the way. However, not all projects have achieved recognition and support for these tokens.
A considerable number of the Solana memecoins launched in the last two months have left investors empty-handed. The latest culprit is the recently launched Bonk Killer (BONKKILLER), which became the hottest topic on Monday for the wrong reasons.
The token surpassed the $100 trillion market capitalization only a few hours after launching. Nonetheless, the reason behind what could have been the most impressive feat in crypto history is no other than a honeypot scam.
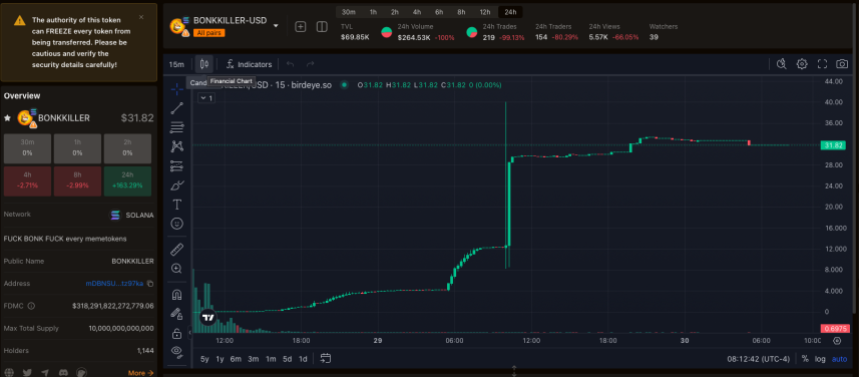
As reported by SolanaFloor, the memecoin is a scam token that attracts investors with high-profit potential but prevents them from selling their holdings. Many realized they couldn’t move their tokens only after the project’s creator activated the “freeze authority.”
This action allowed the creator to avoid selling the token, which skyrocketed the market capitalization metric to $328 trillion. According to analytics platform Birdeye, the Solana-based memecoin registers a $318 trillion market cap at the time of writing.
It’s worth noting that the token isn’t backed by the amount reflected in the metric. As one X user pointed out, the token is worthless if you cannot sell it.
When you buy but can't sell. #bonkkiller pic.twitter.com/AjJokgptmw
— Bull.BnB (@bull_bnb) April 30, 2024
Unfortunately for investors, the creator didn’t use the freezing authority to boost the token’s market cap. The scammer took advantage of the function and stole nearly half a million dollars in BONKKILLER and SOL tokens.
The creator, who holds around 90.8% of the total supply, removed 30,500 BONKILLER and 1,561 SOL, worth around $420,000. According to Birdeye data, the token is valued at $32.81 as of This writing.
UPDATE: @solana memecoin BONKKILLER, a scam and honeypot token, has withdrawn liquidity worth over 3,000 $SOL after freezing token sales for users. pic.twitter.com/JO3E3RuXMW
— SolanaFloor | Powered by Step Finance (@SolanaFloor) April 30, 2024
Even after the community’s warning, some investors continued to buy the project. In the last 12 hours, investors have spent nearly $40,000 on the token. As some X users pointed out, the false market cap might be misleading inexperienced investors into buying the memecoin.
Although it’s not the first scam of this type, the increasing rate of new launches turning fraudulent seems alarming. As reported by NewsBTC, $27 million vanished over the last month after 12 projects were abandoned by their creators.
Ultimately, this incident highlights the importance of thoughtfully researching a project’s background and carefully deciding whether the possibility of massive gains outweighs the risks.
A new rug pull alert sounded on Tuesday after crypto detective ZachXBT unveiled on-chain details of an alleged hack suffered by an NFT project last month. The project’s CTO announced that a response was in the works but ultimately vanished as criticism grew.
On-chain sleuth ZachXBT revealed the alleged misuse of funds by the CTO of NFT project Nuddies NFT. In a now-deleted post, its CTO Kyle explained that the project was “derugged from its previous founder” and built differently from other NFT projects.
A short investigation into how @kyledegods faked a hack and stole SOL from his project @NuddiesNFT before spending it on NFTs and lying to holders about how devastated he was about the incident.
On March 3, 2024 Kyle made a post in his Discord server claiming his wallets had… pic.twitter.com/4ne6dtVyA5
— ZachXBT (@zachxbt) April 2, 2024
According to the crypto detective, Kyle faked a hack that seemingly stole the project’s funds. On March 3, the alleged culprit posted on the Nuddies NFT Discord server, informing us of the hack.
The post affirmed that Kyle’s Mac was hacked despite “not clicking in any malicious link.” The CTO concluded that a “zombie process” was on his computer for an undetermined period.
This “mini-program” gave control of the computer to “the hacker.” Through the TeamViewer app the attacker gained access to the project and Kyle’s wallets. The post further explained that 90 SOL, approximately $17,000 at today’s price, were taken from the Nuddies NFT creator wallet.
Moreover, the hacker allegedly took control of Kyle’s Discord and stole 150 SOL, worth around $28,300, from his wallets. At the time, he claimed to be “mentally destroyed” by the loss of the project’s treasury money.
Nonetheless, the on-chain data compiled by ZachXBT tells a different story. Per the crypto detective’s post, the CTO allegedly lied to the holders and stole the 94 SOL, worth $12,000, when the incident occurred.
The post reveals that the funds were transferred during that day from the Nuddies Royalty Wallet to an exchange deposit at 8:20 UTC. The on-chain investigator claims that a destination transaction was found using time analysis. The transaction to one of Kyle’s wallets accounted for 3.42 ETH, around $11,700, at 8:21 UTC.
The ETH was seemingly used to buy two NFTs: DeGods 2921 and y00t 10991. The DeGod NFT was used as the CTO’s profile picture on X until yesterday.
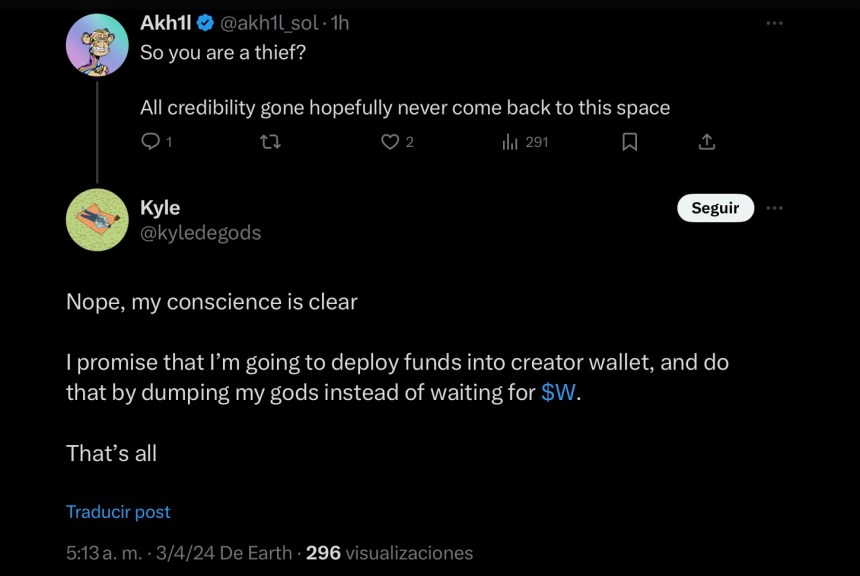
The accusations didn’t go unnoticed by the suspect, who posted on his X account that he was “preparing the answer” with a wink face emoji. After changing his profile picture, Kyle answered some users’ questions about his credibility, to which he replied that his “conscience is clear.”
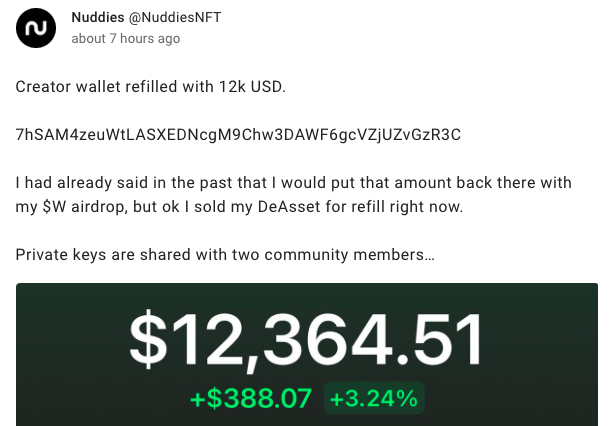
In the early hours of Wednesday, Nuddies NFT account shared a now-deleted post informing that the creator wallet was “refilled with 12k USD.” In the post, Kyle reassured that his previous claims of intending to refill the wallet were authentic.
The CTO also claimed he was “waiting for his $W airdrop” to fulfill his promise instead of selling his DeAsset. Additionally, he “stepped out” of the project after giving the access keys to two community members.
However, the story doesn’t end there. Kyle and Nuddies NFT’s account were deleted a couple of hours after the post. The Nuddies website seems not to be working, as reported by an X user.
The project’s future is unsure as one of the community members to whom Kyle gave the access keys was unaware of the situation. Juiceddd, an NFT artist, is one of the two people in charge of the project.
The artist explained that he was responsible for redrawing the entire Nuddies collection while adding “70+ new traits.” Moreover, Juiceddd stated that he “woke up this morning to being the owner of everything.” The artist is contemplating giving his perspective on the incident as he considers that it is generally the artist who “gets fucked” in these situations.
In the late hours of Tuesday, Trezor’s X account was compromised. The hacker used the hardware wallet company account to promote a fake crypto presale with a malicious link attached.
Members of the crypto community quickly realized the suspicious activity from the company and alerted other X users about the scam. Since then, Trezor’s team has regained control of the account.
In the now-deleted tweets, the hacker announced that Trezor was “willing to support the $SLERF Community.” Taking advantage of the ongoing efforts from crypto projects and exchanges to raise funds for the affected participants of the Slerf presale debacle.
Community alert: Trezor X/Twitter account is currently compromised pic.twitter.com/hNm2OUjEgE
— ZachXBT (@zachxbt) March 19, 2024
The unauthorized post offered the presale of a fake $TRZR token, which required interested users to send SOL to the hacker’s address. Additionally, Trezor supporters would receive a “separate bonus airdrop” if they went to a website linked in the post.
As it’s customary for phishing scams, the link would redirect to a wallet drainer that takes control of the person’s wallet after they try to “claim the airdrop tokens.”
The crypto community shared their thoughts on the hack. A user pointed out that the security breach was a “bad look” for the company as it focuses on crypto security. Others thanked the users who warned about the hack since it potentially saved them and others from falling for it.
It’s worth noting that many users have raised their concerns about the community’s reaction to the Slerf presale drama. They consider that raising funds for the participants affected sets a precedent of “bailing out” bad actors and will only “enable” similar behavior.
Moreover, scammers have been trying to prey on the community’s good faith to help potential victims and newcomers. As seen with the Trezor hack, the scammer seemingly tried to maximize its gains by utilizing the presale meta trend and the Slerf drama.
Usually, the recounting of crypto hacks ends with staggering figures being stolen, but for once, the tale is different. As reported by ZachXBT, the hacker managed to steal $8,100 from the unauthorized post, which includes the 25% drainer fee. As part of the loot, the hacker also received a “whooping 0.96 Solana,” as another user pointed out.
Many wondered if the small amount stolen was due to the community intelligently recognizing the scam or the hacker’s inability to perform a big heist. Whatever the case, this is a remarkable feat as the cold wallet company amasses over 200,000 followers that momentarily became potential victims.
— 赤 – 紅色的 (@Ikuma_On) March 20, 2024
Despite this small victory for the community, “It’s $8.1K more than 0,” as one user said. This raises the question of whether the hack was possible due to a lack of proper security measures or an inside job taking place.
No official explanation has been given yet. Nonetheless, Trezor acknowledged the hack in an X post earlier today.
Alert
We experienced a security incident on our X/Twitter account overnight, despite robust protections including a strong password and 2FA. We continue to investigate.
Please remain vigilant and remember, Trezor will NEVER request funds or assets be sent to any address.…
— Trezor (@Trezor) March 20, 2024
The company affirmed that the hack happened despite its “robust protections,” including two-factor authentication (2FA). At the time of writing, Trezor is continuing its investigation. The statement closed with a message for all users to “remain vigilant.”
According to the blockchain analytics platform Lookonchain, a crypto trader suffered a phishing attack that swooped over 180 million BEAM tokens on Wednesday and affected the token’s price.
In an X (former Twitter) post, Lookonchain exposed a new crypto scam that had occurred on February 15. As the analytics platform detailed, the address 0x83664B8a83b9845Ac7b177DF86d0F5BF3b7739AD, under the name ‘Kirilm.eth’, suffered a phishing attack that led to the theft of millions of BEAM tokens.
kirilm.eth was phishing attacked and lost 180.25M $BEAM($5.14M) 13 hours ago.
The scammer quickly sold the 180.25M $BEAM for 1,629 $ETH($4.6M), which caused the price of $BEAM to drop by ~7%.https://t.co/x8epiNx4Qa pic.twitter.com/ytcfYib2Kg
— Lookonchain (@lookonchain) February 16, 2024
Users seemingly identified the victim as a crypto trader named Kirill Marinov. According to the information provided, the victim lost 180.25 million BEAM tokens, worth approximately $5.14 million, to an account labeled as ‘Fake_Phishing291038.’
Shortly after the theft, the scammer’s address liquidated the total amount of stolen BEAM tokens, exchanging them for 1,629 ETH worth approximately $4.6 million.
According to Web3 anti-scam platform Scam Sniffer, the victim signed an ‘increase allowance’ transaction that gave the scammer access to the tokens. Additionally, the. X post detailed that the token spender is a Safe Wallet address.
However, this writing has not revealed further details about the victim, the exact tactics used by the scammer, and their identity.
Phishing scams are among the most popular tactics for crypto-related crimes. Scammers exploit inexperienced investors’ naivety and oversights from more experienced traders to gain access to the funds.
The scamming tactics involve a variety of ways to trick the victims into revealing their private keys or login information to grant access to the victim’s wallets. Due to this, experts urge all crypto investors to stay alert and take the necessary measures to keep their assets safe.
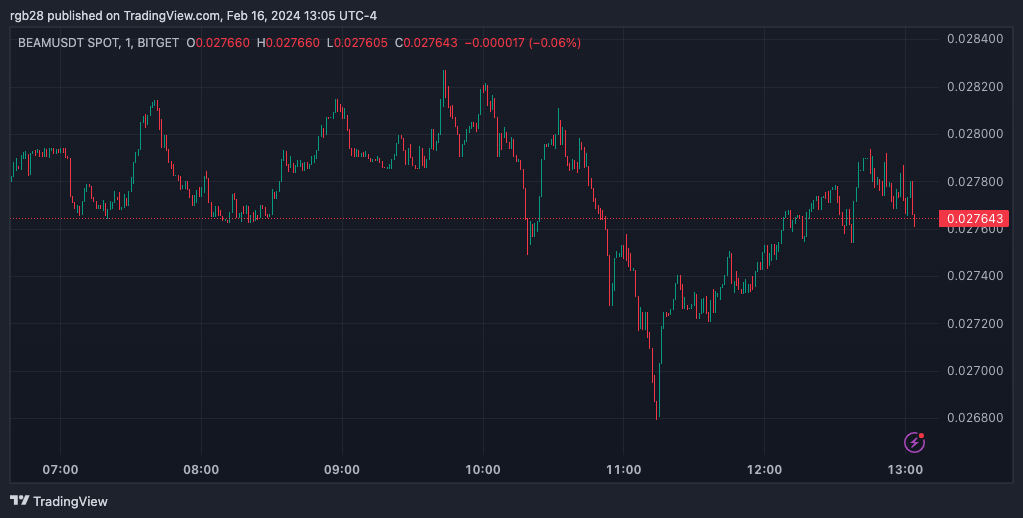
The BEAM token serves as the native crypto asset for the Beam network. After the heist and subsequent exchange to ETH, the token’s price dropped, falling from the $0.030 price level to the $0.028 range.
Beam Network is a gaming network powered by the Merit Circle DAO. The ecosystem brings developers and gamers together to develop the gaming industry further. According to the Beam team, “At its core, Beam aspires to create harmony between gamers and developers.
It’s not just about gaming; it’s about ownership, empowerment, and a global community. Every feature and tool is a step towards this visionary future.”
At writing time, the token trades at $0.027, representing a 2.4% drop in the last hour and a 9.3% decrease from its trading price in the previous 24 hours. According to CoinMarketCap data, the token’s daily trading volume saw a 25.7% decrease in the last 24 hours, sitting at the #104 spot on this metric with $61.4 million.
Despite the negative price reaction following the scam, the BEAM price still registered a 32.9% increase in the last 7 days. Similarly, BEAM’s trust score in the spot markets remains untouched, per CoinGecko Data.
According to a recent report published by crypto analytics firm Chainalysis, money laundering involving crypto assets has experienced a notable decline compared to the previous year. However, the report highlights that illicit actors have started adapting their tactics to evade detection and further obscure the movement of illicit funds.
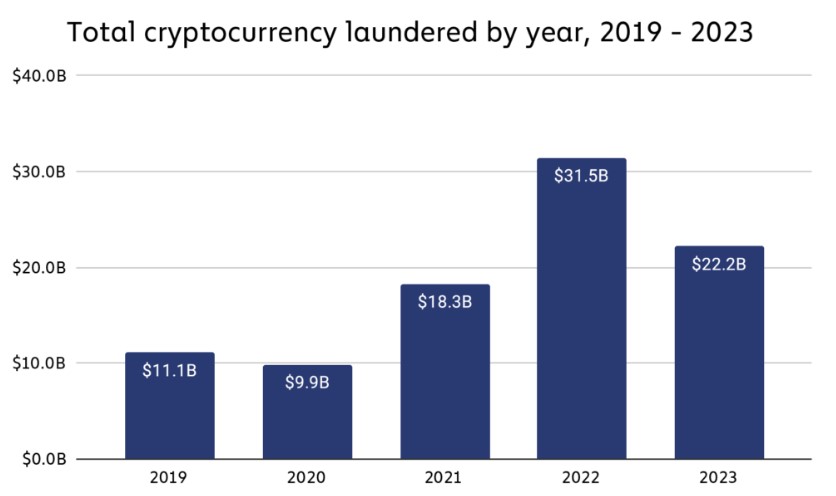
According to the report, illicit addresses sent approximately $22.2 billion worth of cryptocurrency to various services in 2023, a significant decrease from the $31.5 billion sent in 2022.
While part of this decline can be attributed to an overall decrease in legitimate and illicit crypto transaction volume, the report reveals that money laundering activity witnessed a steeper drop of 29.5%, compared to the 14.9% decrease in total transaction volume.
Centralized exchanges remain the primary destination for funds originating from illicit addresses, with this trend remaining relatively stable over the past five years. However, the report indicates a shift in the distribution of illicit funds, with a growing share being directed towards decentralized finance (DeFi) protocols.
Chainalysis suggests that this can be attributed to DeFi’s overall expansion during the same period, although the transparent nature of DeFi platforms makes them less favorable for obfuscating fund movements.
While the breakdown of service types used for money laundering in 2023 resembled that of the previous year, there were noticeable changes in specific types of crypto criminals’ money laundering practices.
The report highlights a significant increase in the volume of funds sent to cross-chain bridges from addresses associated with stolen funds, indicating a shift towards utilizing bridge protocols for money laundering purposes. Additionally, there was a substantial rise in funds sent from ransomware attacks to gambling platforms and bridges, showcasing the “adaptability and resourcefulness” of cybercriminals.
The concentration of money laundering at fiat off-ramps, where criminals convert their crypto into cash, remains a significant concern. While thousands of off-ramping services operate, most money laundering activity is concentrated in a few services.
In 2023, 71.7% of illicit funds sent to off-ramping services went to just five services, a slight increase from 68.7% in 2022. The report also reveals an increase in deposit addresses receiving large sums of illicit cryptocurrency, indicating a more diversified approach by criminals to evade detection and mitigate the impact of frozen accounts.
Furthermore, the report highlights the changing tactics of “sophisticated” crypto criminals, particularly in the case of North Korean-affiliated hacking groups like Lazarus Group.
According to Chainalysis, these actors have demonstrated an ability to adapt their money laundering strategies in response to law enforcement actions. The report cites the shutdown of mixer services, such as Sinbad, and the subsequent rise of replacements like YoMix, which has become a preferred mixer for North Korea-affiliated hackers.
Moreover, cross-chain bridges have seen substantial growth in money laundering activities, with illicit actors leveraging these protocols to move funds between blockchains. North Korean hackers, in particular, have been prominent users of bridge protocols for money laundering purposes.
Ultimately, the report emphasizes the need for increased diligence and understanding of “interconnectedness” in fighting crypto crime by targeting money laundering infrastructure.
Featured image from Shutterstock, chart from TradingView.com
On January 23, Wallet Connect and other web3 companies informed their users about a phishing scam using official web3 companies’ email addresses to steal funds from thousands of crypto wallets.
Wallet Connect took X to notify its community about an authorized email sent from a Wallet Connect-linked email address. This email prompted the receivers to open a link to claim an airdrop, however, the link led to a malicious site and, as Wallet Connect confirmed, it was not issued directly by the team or anyone affiliated. Wallet Connect contacted web3 security and privacy firm Blockaid to investigate the phishing scam further.
We've detected a sophisticated phishing attack impersonating @WalletConnect via a fake email linking to a malicious dapp.
Blockaid enabled wallets are safe.https://t.co/quz9olGrpZ pic.twitter.com/TYS0BjIk2J
— Blockaid (@blockaid_) January 23, 2024
In the following hours, crypto sleuth posted a community alert to inform unaware users that CoinTelegraph, Token Terminal, and De.Fi team emails were also compromised, signaling that a massive and more sophisticated phishing campaign was happening. At the time of the post, around $580K had been stolen.
After investigating, Blockaid later revealed that the attacker “was able to leverage a vulnerability in email service provider MailerLite to impersonate web3 companies.”
Email phishing scams are common among cyber scammers, making users wary of most suspicious links or emails. At the same time, companies and entities advise against opening links that do not come from their official channels. In this case, the attacker was able to trick a vast number of users from these companies as the malicious links came from their official email addresses.
The compromise allowed the attacker to send convincing emails with malicious links attached that led to wallet drainer websites. Specifically, the links led to several malicious dApps that utilize the Angel Drainer Group infrastructure.
The attackers, as Bloackaid explained, took advantage of the data previously provided to Mailer Lite, as it had been given access by these companies to send emails on behalf of these sites’ domains before, specifically using pre-existing DNS records, as detailed in the thread:
Specifically, they used “dangling dns” records which were created and associated with Mailer Lite (previously used by these companies). After closing their accounts these DNS records remain active, giving attackers the opportunity to claim and impersonate these accounts. pic.twitter.com/cbTpc5MXu1
— Blockaid (@blockaid_) January 23, 2024
The explanation later came Via an email, where MailerLite explained that the investigation showed that a member of their customer support team inadvertently became the initial point of the compromise. As the email explains:
The team member, responding to a customer inquiry via our support portal, clicked on an image that was deceptively linked to a fraudulent Google sign-in page. Mistakenly entering their credentials there, the perpetrator(s) gained access to their account. The intrusion was inadvertently authenticated by the team member through a mobile phone confirmation, believing it to be a legitimate access attempt. This breach enabled the perpetrators) to penetrate our internal admin panel.
MailerLite further adds that the attacker reset the password for a specific user on the admin panel to consolidate the unauthorized control further. This control gave them access to 117 accounts, of which they only focused on cryptocurrency-related accounts for the phishing campaign attack.
An anonymous Reddit user posted an analysis of the situation and gave a closer look at the attacker’s transactions. The user revealed:
One victim wallet appears to have lost 2.64M worth of XB Tokens. I’m showing about 2.7M sitting in the phishing wallet of 0xe7D13137923142A0424771E1778865b88752B3c7, while 518.75K went to 0xef3d9A1a4Bf6E042F5aaebe620B5cF327ea05d4D.
The user stated that most stolen funds were in the first phishing address. At the same time, approximately $520,000 worth of ETH were sent to privacy protocol Railgun, and he believes that they will soon be moved through another mixer or exchange.
Denver-based internet pastor, Eli Regalado, is at the center of a controversy surrounding an alleged crypto Ponzi scheme involving INDX coin.
The self-proclaimed spiritual leader has come under scrutiny as Colorado’s securities regulator investigates his deceptive practices, which reportedly resulted in over $3 million in ill-gotten gains. Fortune magazine report shed light on the matter, exposing Regalado’s questionable actions and shedding light on the plight of the victims involved.
According to Colorado’s securities regulator, Regalado, and his wife orchestrated a “small-scale swindle”, targeting hundreds of individuals with promises of extraordinary returns on their investments in INDX coin.
Presenting his appeals with biblical undertones, using terms like “sowing” and “tithing,” Regalado convinced his online church followers that purchasing the cryptocurrency would yield a tenfold increase in their investments.
However, the promised returns never materialized, and investors lost their “hard-earned” money. To compound matters, it is alleged that the Regalados diverted a significant portion of the funds to finance personal expenses, including home renovations and luxury purchases, further exacerbating the victims’ financial losses.
Despite the allegations and mounting legal troubles, Regalado chose to address the accusations head-on by posting a 10-minute video on the crypto project’s website.
In the video, he attempts to deflect responsibility, claiming that misappropriating funds was not solely his decision, but rather a result of divine guidance for a home remodeling project.
Displaying a lack of understanding of financial concepts, Regalado haphazardly employs buzzwords like “leverage” and “liquidity” without demonstrating a clear comprehension of their meaning.
Furthermore, Regalado boasts about the supposed success of the project, mentioning “$300 million of coins sown before the exchange went live.” However, the Colorado regulator clarifies that these coins have no value, primarily because they could only be traded on the Kingdom Wealth Exchange, an ill-functioning service operated by the Regalados themselves.
According to Fortune, the next steps in this ongoing investigation are expected to involve the state of Colorado seizing any remaining funds and returning them to the defrauded investors.
Meanwhile, Regalado’s video attempts to invoke divine intervention, predicting that the INDX coin debacle will resolve itself miraculously through divine intervention in the financial sector.
According to CoinGecko data, the total crypto market cap has declined over 4.6%, reaching as low as $1.51 trillion on Monday. However, when compared to one year ago, the cryptocurrency market has witnessed an impressive surge of 55.27%.
At the forefront of the cryptocurrency market stands Bitcoin (BTC), the pioneering digital currency that continues to dominate the landscape. As of today, Bitcoin’s market cap stands at an impressive $795 billion, accounting for a substantial 47.66% of the total cryptocurrency market.
Featured image from Shutterstock, chart from TradingView.com
2023 started with a challenging overall landscape for the crypto market that continued throughout the rest of the year. However, the market saw a recovery with a spike in bullish sentiment and ended the year on a positive note.
Additionally, 2023 saw a decline in crypto scamming and crypto-related illicit activity compared to the previous year, as new data shows.
American blockchain analysis firm Chainalysis released its 2024 Crypto Crime Report detailing the trends and figures that crypto-related illicit activities saw in 2023. The firm’s data shows a significant drop in value received in cryptocurrency addresses used for illicit activities, totaling $24.2 billion.
This is a considerable reduction compared to the 2022 updated estimate of $39.6 billion. In addition, the share of all crypto transaction volume associated with illicit activity reduced from 0.42% in 2022 to 0.34% in 2023.
According to the report, there seems to be a shift in the type of assets involved in crypto-related crime activities over the last two years, with Bitcoin no longer being the most used asset for most illicit transactions.
Alternately, stablecoins have become a more popular choice for crypto assets involved in illicit activities, as the report states. This increase could be attributed to the recent general growth of stablecoins’ share of all crypto activity overall.
The shift to stablecoins is not seen in every related crime, with activities, such as darknet market sales and ransomware extortion, still taking place predominately in Bitcoin.
Nonetheless, it’s worth noting that their issuers can trace stablecoins, and funds can be frozen when addresses are linked to illicit activities, as Tether did back in 2023.
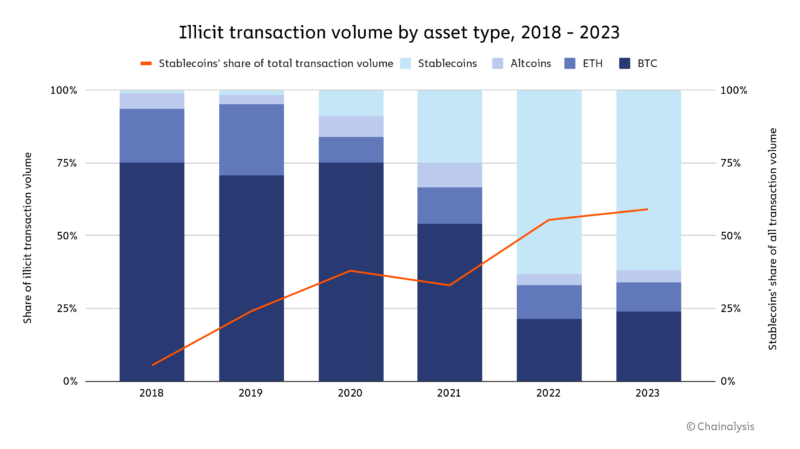
Chainalysis on-chain metrics suggest that scamming revenues have been trending globally since 2021. Although these crimes are still underreported, “overall, scamming is down, given broader market dynamics.”
Romance scams, such as ‘pig butchering,’ are among the most popular crypto scamming tactics used by scammers and are one of the biggest forms of related crime by transaction volume.
Regarding crypto hacking, the firm believes that “the decline in stolen funds is driven largely by a sharp dropoff in DeFi hacking,” it could represent “the reversal of a disturbing, long-term trend.” In 2023, crypto scamming and hacking revenue fell significantly, with the total revenue decreasing 29.2% and 54.3%, respectively.
In contrast to the overall trends, ransomware and darknet markets, two of the most prominent forms of related crime, saw revenues rise in 2023. Similarly, 2023’s growth in darknet market revenue comes after a 2022 decline in revenue.
The report shows that transactions with sanctioned-related entities and jurisdictions drive most of the illicit activity as entities and jurisdictions move towards using stablecoins and other crypto assets to bypass restrictions.
They accounted for a combined $14.9 billion transaction volume in 2023, representing 61.5% of all illicit transactions over the year. Chainalysis explains that:
Most of this total is driven by cryptocurrency services that were sanctioned by the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC), or are located in sanctioned jurisdictions, and can continue to operate because they’re in jurisdictions where U.S. sanctions are not enforced.
Ultimately, the report addresses that not all sanction-related transactions are due to the illicit use of digital assets, as some of that $14.9 billion volume is related to the average users who reside in the sanctioned jurisdictions.
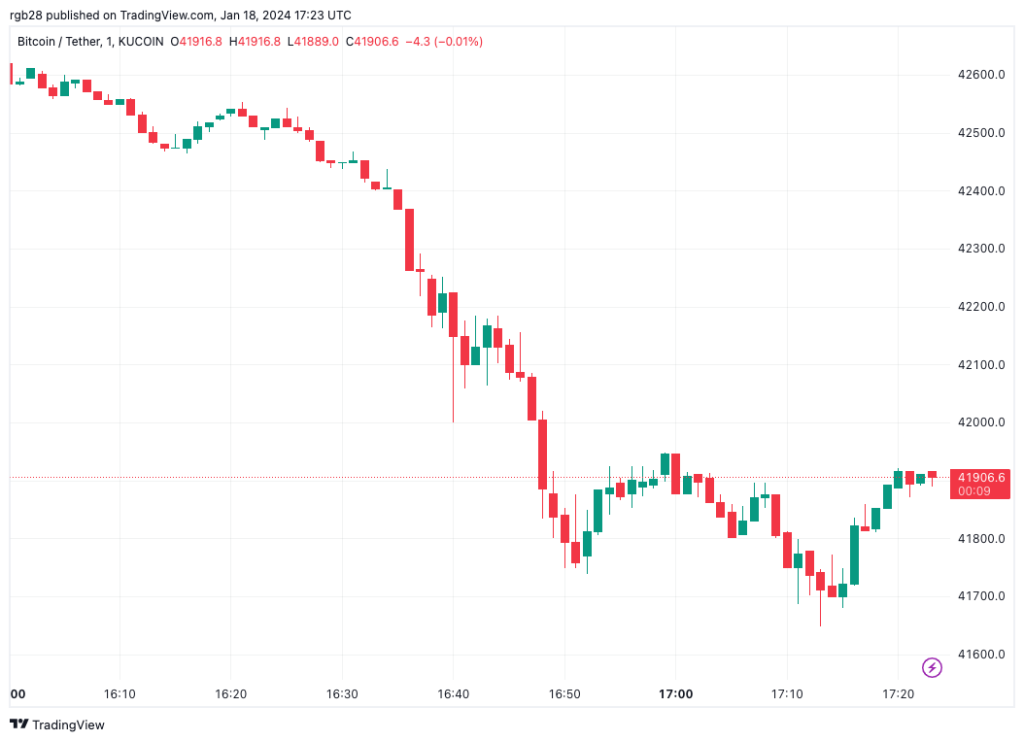
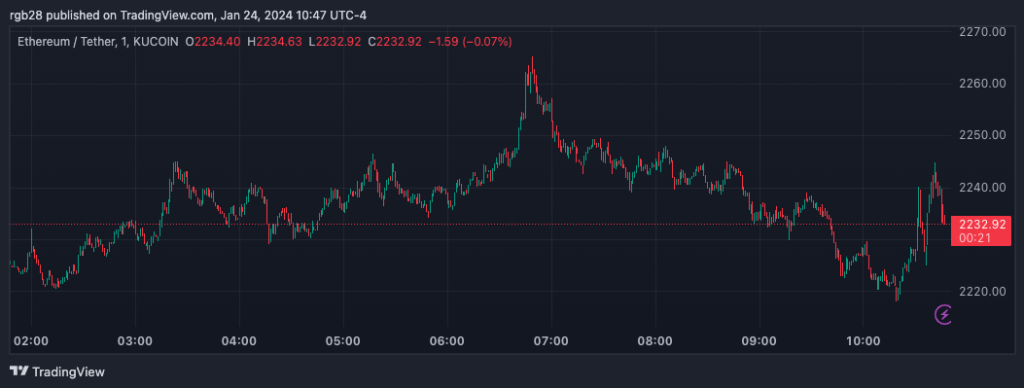
Bitcoin trading at $41,906.6 on the hourly chart. Source BTCUSDT on TradingView.com
In a recent investigation by The Guardian, alarming details have emerged regarding a crypto project, HyperVerse, that allegedly lost $1.3 billion of investors’ funds.
The report reveals that the chief executive officer promoted by the project, supposedly backed by celebrity endorsements including Chuck Norris, appears to be absent.
HyperVerse, promoted by Australian entrepreneur Sam Lee and his business partner Ryan Xu, founders of the now-collapsed Australian Bitcoin (BTC) company Blockchain Global, has been scrutinized for its deceptive practices. The project attracted thousands of investors, who ultimately lost millions of dollars.
The investigation raises concerns about the legitimacy of HyperVerse’s CEO, as the qualifications and credentials attributed to the supposed chief executive, Steven Reece Lewis, have no basis.
Promotional material released for HyperVerse claimed that Lewis graduated from the University of Leeds and held a master’s degree from the University of Cambridge. However, neither institution has any record of his existence.
Furthermore, there are no records of Lewis on the UK companies register, Companies House, or the US Securities and Exchange Commission (SEC). Interestingly, Adobe, a publicly listed company, also has no record of any acquisition involving a company owned by “Steven Reece Lewis.”
The report indicates that HyperVerse managed to secure celebrity endorsements, including video messages of support from Steve Wozniak, co-founder of Apple, and actor Chuck Norris.
However, it is unclear how these messages were obtained, as all four celebrities mentioned in the report are available for hire through Cameo, where individuals can pay to have high-profile individuals read scripted messages.
The investigation also highlights regulatory concerns, as HyperVerse operated without significant scrutiny in Australia despite being flagged by regulators overseas as a possible scam or suspected pyramid scheme.
The Australian Securities and Investments Commission (ASIC) has been referred to the case but has not yet taken action.
Investors in HyperVerse were lured with promises of substantial returns and the opportunity to explore a new digital metaverse similar to Facebook. However, the scheme ultimately resulted in significant losses for investors, estimated at $1.3 billion in 2022, according to blockchain analysts Chainalysis.
The Guardian’s findings shed light on the deceptive practices employed by HyperVerse and raise questions about the responsibilities of regulators in overseeing such projects.
As the aftermath of this cryptocurrency scandal unfolds, investors and authorities alike are left grappling with the consequences of a scheme that capitalized on false claims and celebrity endorsements to defraud unsuspecting individuals.
Featured image from Shutterstock, chart from TradingView.com
In a startling revelation by Scam Sniffer, the cryptocurrency world has been hit hard by a series of sophisticated phishing scams in 2023. The team behind the crypto security tool has reported that Wallet Drainers, a type of malware, have successfully siphoned off nearly $295 million from approximately 324,000 unsuspecting victims in the space.
These malicious software programs, predominantly found on phishing websites, trick users into authorizing harmful transactions, leading to significant asset theft from their crypto wallets.
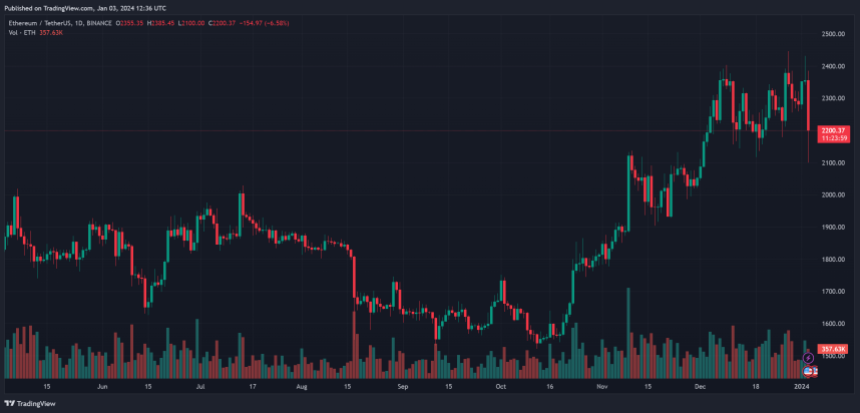
A closer examination of the data reveals a worrying trend of increasing phishing activities; each correlated with specific events in the crypto space. For instance, a significant theft of almost $7 million was reported on March 11, coinciding with fluctuations in USDC rates and an impersonation scam of Circle, the company behind the stablecoin.
Additionally, a noticeable theft spike was observed around March 24, aligning with the hacking of Arbitrum’s Discord and its airdrop date. Scam Sniffer’s report highlighted several notable Wallet Drainers, including Inferno Drainer, which alone stole $81 million from 134,000 victims, and MS Drainer, with a haul of $59 million from 63,000 victims.
The report notes the alarming scale and velocity of these operations. For example, Monkey Drainer extracted $16 million over six months, whereas Inferno Drainer looted $81 million in just nine months, as seen in the chart below. The report also sheds light on the common phishing signatures these Drainers use.
Depending on the type of assets in a victim’s wallet, various phishing methods are deployed, ranging from increased allowance to ERC20 permit signatures. The most severe cases involved victims losing millions to these sophisticated scams.

Scam Sniffer has ramped up its efforts in response to this growing threat. Over the past year, the tool scanned nearly 12 million URLs, identifying close to 145,000 as malicious. Furthermore, its open-source blacklist contains nearly 100,000 dangerous domains, continuously updated to platforms like Chainabuse.
The increasing use of smart contracts by scammers, such as multicall for efficient asset transfers and CREATE2 & CREATE functions to bypass wallet security checks, marks a significant change from the previous year. This evolution underscores the need for enhanced vigilance and updated security measures in the crypto community.
Scam Sniffer’s work extends beyond just tracking and reporting. The team actively collaborates with well-known platforms, offering its services to their users. They encourage all stakeholders in the crypto ecosystem to “join the fight against phishing, emphasizing that security is a collective responsibility.”
In closing, Scam Sniffer acknowledges the support of its community:
(…) crypto phishing involves multiple parties, crypto, and non-crypto platforms. Security requires a collective effort. If you wish to enhance your product’s capabilities in this area, please contact us at b2b@scamsniffer.io.
Finally, thanks to all the supporters of Scam Sniffer! Your support is the motivation that keeps us going.
Cover image from Unsplash, chart from Tradingview
In the non-fungible tokens (NFTs) sector, scammers are constantly devising new methods to exploit unsuspecting collectors. The latest incident involves fraudsters posing as journalists from Forbes magazine, specifically targeting Bored Ape Yacht Club (BAYC) NFT holders.
One BAYC owner, “Crumz,” recently shared his encounter with these scammers, detailing the elaborate scheme designed to steal his digital assets.
According to Crumz, the scam began when he received a direct message on X (formerly Twitter) from someone claiming to be a Forbes editor named Robert Lafranco.
Intrigued by the prospect of being featured in an article about BAYC, Crumz proceeded cautiously, conducting a cursory online search that seemingly confirmed the person’s identity. Unbeknownst to him, the scammers had meticulously crafted a “facade of credibility.”
The supposed Forbes journalist informed Crumz of their interest in gathering firsthand accounts from BAYC owners regarding their experiences within the club. Despite initial surprise at being approached, Crumz agreed to participate in a scheduled Zoom call.
Crumz further stated that the scammers failed to show up for the initial call, citing a fabricated family emergency as the reason for their absence. They rescheduled the meeting for a later date.
When the rescheduled call finally took place, Crumz noticed several red flags. The individuals on the call refused to activate their cameras, claiming technical difficulties.
Another person claiming to be Steven Ehrlich, Forbes’ research director, joined the conversation. Crumz shared his BAYC journey, recounting the early days and highlighting the club’s unique features.
During the call, Crumz alleges that the scammers exhibited further suspicious behavior. They lacked a premium Zoom account and insisted on using multiple call links.
Additionally, they requested permission to record the screen using a separate recording bot. Although Crumz initially thought nothing of it, alarm bells rang when they asked him to find a banana and say something that resembled his Bored Ape character.
Unable to produce a banana on the spot, Crumz excused himself momentarily, muting his screen. During this momentary lapse, the scammers attempted to take control of his computer, prompting him to intervene when they navigated to the website delegate.cash.
Ultimately, all of Crumz’s valuable NFTs were securely stored in cold storage, safeguarding them from potential theft. He promptly shut down his computer to ensure his safety, hoping to sever any remote access the scammers may have gained. Crumz concluded:
Hopefully I’m safe now. Don’t think they can still control my computer when I turn it back on. Please be safe out there, it could’ve been a dreadful day today
BAYC has recently witnessed a notable decline in various key metrics. The latest NFT data reveals a decrease in the number of sales, sales volume, and primary sales.
According to the latest figures, the number of sales has seen a significant drop of 33.59%, with 87 sales reported at present compared to 131 sales recorded the previous day.
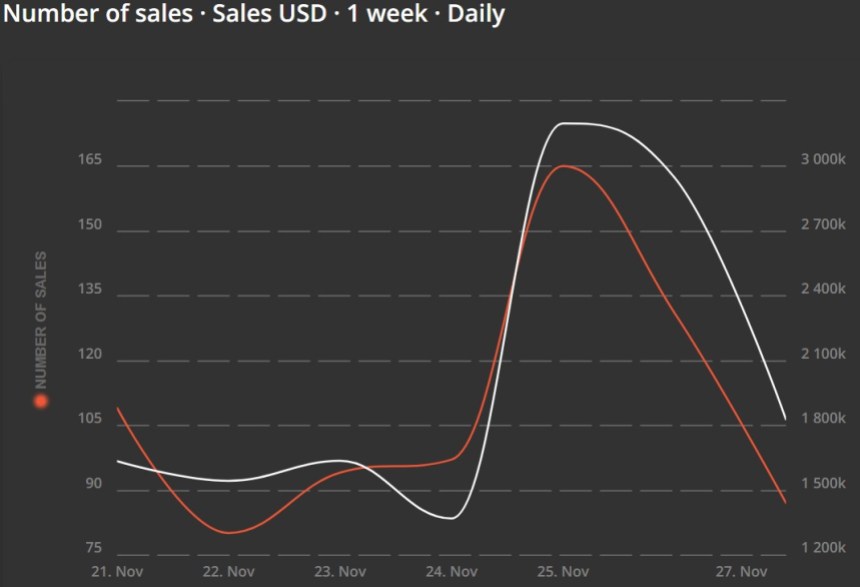
This decrease in sales has also resulted in a decline in sales in USD, with a decrease of 38.02%. The current sales volume is $2 million, compared to $3 million on Sunday.
In terms of sales volume, primary sales have experienced a 100% decrease, with no current sales reported. In contrast, primary sales generated $12,000 in USD the previous day. Secondary sales volume has also declined 37.76%, with the current figure at $2 million, compared to $3 million from the previous day.
Featured image from Shutterstock, chart from TradingView.com
Grok (GROK) token, inspired by Elon Musk’s artificial intelligence service through X (formerly Twitter), has recently come under scrutiny following explosive growth in market capitalization.
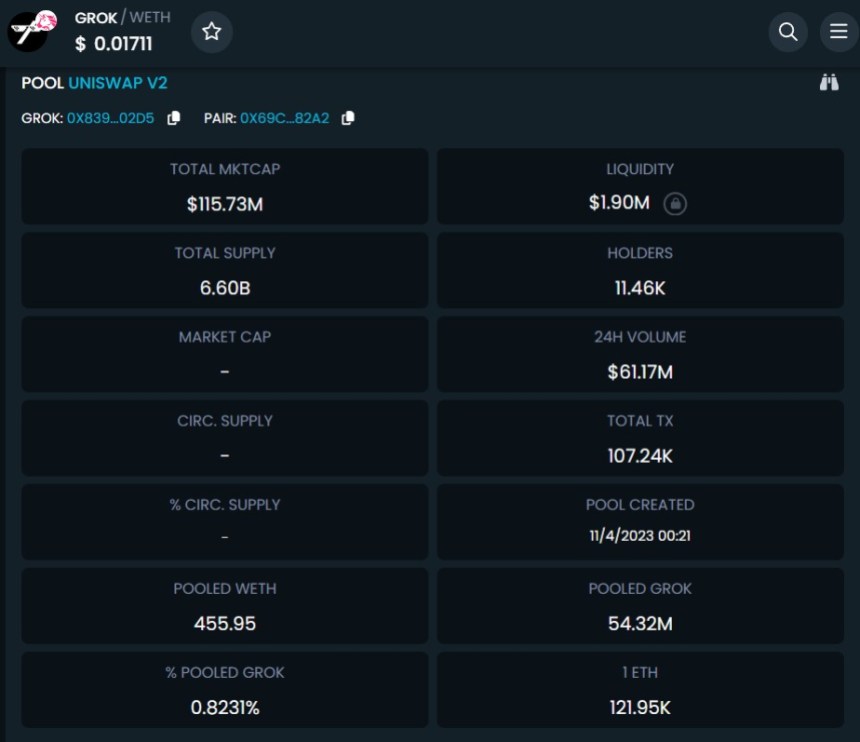
According to recent reports, Grok zoomed to a staggering $160 million market cap within just eight days of its release. However, reports of alleged scam involvement have overshadowed the token’s rapid ascent.
Grok token prices have soared, doubling within the past 24 hours alone, extending a week-long rally that has seen an astonishing 13,000% increase. The token boasts an impressive 11,000 holders and has witnessed a trading volume of over $60 million over the past 24 hours, according to data from DEXTools.
However, ZachXBT, a self-proclaimed crypto detective, has raised concerns about the legitimacy of Grok, stating that the token was created by a scammer. ZachXBT has stated that the same X/Twitter account associated with Grok has been linked to at least one other fraudulent scheme. ZachXBT stated:
Not that people in this space will care but GROKERC20 GROK was created by a scammer. Same exact X/Twitter account has been reused for at least one other scam. X/Twitter ID: 1690060301465714692
Satoshi Flipper, another prominent crypto trader on X, echoed this sentiment, labeling Grok as an “effing scam” and emphasizing that Elon Musk did not authorize the token’s launch. Satoshi Flipper said:
This is Grok. $1.9M liquidity and a $137M market cap? What an effing scam. Not only that, it’s completely fraudulent to trade this knowing Elon Musk, the owner of Grok, did not authorize these devs to launch a token. Imagine touching this toxic trash.
Experts from Arkham Intelligence also weighed in, reporting that an on-chain trader sold a significant amount of GROK at nearly 40% slippage, reinforcing the scam allegations made by ZachXBT.
The controversy surrounding Grok has raised concerns within the cryptocurrency community. Critics argue that the token’s market cap, coupled with the lack of authorization from Elon Musk, raises red flags.
The token’s market cap has undergone a retracement, now at $108 million, down from its previous value of $160 million. Additionally, the token exhibits a liquidity of $1.83 million.
Despite experiencing a substantial slippage of 48%, with its price dropping as low as $0.0056000, the token has remarkably recuperated and is now trading at $0.0108452.
It is yet to be determined whether further reports will surface to shed light on the individuals behind the token’s creation and their objectives, potentially exposing the risk of a rug pull within the cryptocurrency industry.
However, despite these allegations, the token has attracted significant attention and excitement from investors eager to participate in the potential surge of the next major meme coin, aiming to achieve substantial gains in their investments. As of the time of writing, the Grok official account on X has not made any statements regarding these allegations.
Featured image from Shutterstock, chart from TradingView.com
In a chilling development on Halloween Day, the crypto community was hit with disturbing news as PeckShield, a renowned blockchain security company, revealed a series of rug pulls over the past few hours.
Rug pulls, a form of cryptocurrency scam, involve sudden and deliberate value drops in specific tokens, accompanied by the perpetrators swapping the native tokens for Ethereum (ETH). The meme coins affected by the rug pulls were identified as MEME, MEMEPAD, and TITANX.
According to PeckShield’s X (formerly Twitter) post, the MEME token on the Ethereum blockchain experienced a jaw-dropping 100% drop in value. The address 0xBd72…5871 was responsible for swapping a staggering 4,854,740,126,240,000 MEME tokens for approximately 43.68 ETH.
It is important to note that the rug pull token shared the same name as the legitimate MEME token, adding to the confusion.
Similarly, the MEMEPAD token on Ethereum suffered an identical 100% value drop. The address 0xBd72…5871 conducted a swap of 4,854,740,126,240,000 MEMEPAD tokens for around 44.84 ETH.
Once again, the fraudulent crypto rug pull shared the same name as the genuine MEMEPAD token, compounding the deceitful nature of the scam.
Additionally, the TITANX token launched two days ago, October 28, on Ethereum experienced a staggering 100% value decline.
The address 0xBd72…5871 executed a swap of 4,854,740,126,240,000 TITANX tokens for approximately 46 ETH. Mirroring the previous instances, the rug pull token masqueraded under the same name as the legitimate TITANX crypto token.
In alarming events, the Fantom (FTM) Foundation finds itself entangled in a harrowing tale of fund drains and swift token swaps. PeckShield has reported two significant incidents involving the Fantom Foundation’s finances, leaving the organization with substantial losses.
The first incident occurred on October 17, 2023, when wallets associated with the Fantom Foundation were drained of approximately $7 million worth of cryptocurrencies, equivalent to around 4,500 ETH.
Additionally, on October 26, the Fantom Foundation faced another devastating event. An unidentified entity, the “Fantom Foundation Drainer,” executed a bold move by swapping a staggering 8,087,377.97 DAI for 4,560.52 ETH.
The gravity of the situation intensified when the Fantom Foundation Drainer swiftly executed another swap on October 30, converting the 4,560.52 ETH back into approximately 8.3 million DAI within a mere 30 minutes.
The Fantom Foundation is now faced with the daunting task of investigating the breaches, identifying the culprits, and fortifying its security infrastructure to prevent future incidents.
Despite recent developments, the native token of the Fantom protocol, FTM, is trading at $0.2388, reflecting a 1% increase in the past 24 hours.
Notably, the token has experienced a substantial surge across various time frames. Presently, it has maintained an upward trend, with gains of over 6% and 30% in the seven-day and fourteen-day periods, respectively.
Over the year-to-date period, the token has recorded a 5% increase. These figures indicate the token’s positive performance and growth trajectory.
Featured image from Shutterstock, chart from TradingView.com
As the crypto market continues to attract substantial investments, it has also witnessed a surge in scams and fraudulent activities. Regulatory institutions worldwide, spearheaded by the United States, seem to intensify their efforts to combat cyber threats, hacks, and frauds that affect the industry.
However, the nascent sector is far from the only one suffering from increasing cyber threats. Since 2020, these attacks have been common both within the crypto space and outside.
In line with this, the Federal Bureau of Investigation (FBI) identified a new threat dubbed “The Phantom Menace.” The FBI issued a warning on September 29, alerting the public about the escalating “Phantom Hacker” scams, particularly affecting senior citizens.
The FBI’s statement revealed that the “Phantom Hacker” scam is an evolution of traditional tech support scams, employing imposter tech support, fraudulent exchange account support, and government personas to gain victims’ trust. This multi-layered approach helps scammers identify lucrative accounts to target.
From January to June 2023, the FBI Internet Crime Complaint Center (IC3) received over 19,000 complaints about tech support and crypto scams, resulting in estimated losses exceeding $542 million. Losses have already surpassed 2022 figures by 40% as of August 2023.
The Scam Phases:
Once victims are connected, scammers manipulate them into downloading software that grants remote access to their computers. By fabricating a fictitious virus scan, scammers deceive victims into believing their computers have been compromised or are at risk.
Subsequently, they coax victims into opening their financial accounts, allowing scammers to identify the most lucrative targets.
The scammers falsely inform victims that foreign hackers have compromised their computers and accounts. To ensure the safety of victims’ funds, they instruct victims to transfer their money to a purportedly “secure” third-party account, often claiming an affiliation with recognized entities like the Federal Reserve or other US government agencies.
These transfers typically involve wire transfers, cash, or even cryptocurrencies, with the funds predominantly sent overseas. Scammers coerce victims into maintaining secrecy regarding the true purpose of these transfers.
In contrast with the alarming rise of “Phantom Hacker” scams, a Chainalysis report indicates an overall decline in cryptocurrency-related crime in 2023. Cumulative daily inflows to known illicit entities have decreased by 65% compared to the same period in 2022.
Notably, scams have experienced the most significant decline, with scammers generating nearly $3.3 billion less revenue in 2023 than in 2022. However, the report highlights a concerning trend: ransomware attacks.
Ransomware attackers extorted $175.8 million more by June 2023 than during the same period in 2022, suggesting a reversal from the downward trend observed in 2022.
While overall crypto-related crime has declined, the resurgence of ransomware attacks poses a significant menace and could spill over to the nascent sector. While the number declines, the amount stolen in the crypto space urging users to remain cautious in the face of new threats.
Featured image from Shutterstock, chart from TradingView.com
The OneCoin scam saga has continued to linger despite it being years since it took place, and this time around, a lawyer who was involved in the pyramid scheme has received a rather shocking response from the court.
According to a report by Bloomberg, a US court has denied Mark Scott’s request to be granted a new trial. The lawyer is said to have helped launder $400 million as part of the proceeds from the scheme and was found guilty by the court in November 2019 of money laundering and bank fraud conspiracy.
However, Scott was hoping to get a new trial on the grounds of “legal mistakes” and following evidence that the prosecution witness, who happens to be the brother of the “cryptoqueen” Ruja Ignatova, perjured himself on the witness stand.
As to the court’s reason for the decision, US District Judge Edgardo Ramos stated that he wasn’t convinced that Scott was innocent despite the fact that Ignatova’s brother, Konstantin Ignatov, lied in his testimony.
The judge may have reached this conclusion because the prosecution provided other irrefutable evidence to the fact that Scott was guilty, and the court’s ruling paves the way for Scott to be sentenced.
However, Bloomberg reports that Scott’s lawyer mentioned that his client intends to appeal the decision. According to him, it is disappointing that the court didn’t grant a new trial despite being provided with “undisputed evidence that the Government’s sole cooperating witness perjured himself.”
Ignatov had himself been prosecuted for his role in his sister’s fraudulent scheme. However, he pleaded guilty and agreed to cooperate with the prosecutor, including testifying against other alleged conspirators like Scott.
On September 12, US District Judge Edgardo Ramos sentenced OneCoin’s co-founder Karl Greenwood to 20 years imprisonment and ordered him to pay close to $300 Million in forfeiture. In the Department of Justice’s (DOJ) statement, Greenwood, alongside Ruja Ignatova, is said to have “operated one of the largest fraud schemes ever perpetrated.”
Karlwood and Ignatova reportedly made over $4 billion from their fraudulent scheme, with many investors worldwide investing their money in the cryptocurrency OneCoin. At the time, Ignotova claimed that crypto would be the “Bitcoin killer.”
The “Cryptoqueen” still remains at large and is listed on the Federal Bureau of Investigation’s (FBI) top 10 most-wanted fugitives. She is also listed as one of the most wanted criminals in Europe, with Europol offering a reward of 5,000 Euros for information leading to her arrest.
The last known fact as to her whereabouts is that she boarded a plane from Bulgaria to Athens and has ‘disappeared’ since then.
In a major development, the US Securities and Exchange Commission (SEC) has charged former New Jersey State Correctional Police Officer, John A. DeSalvo, for allegedly orchestrating a fraudulent crypto fraud scheme that specifically targeted law enforcement personnel.
DeSalvo stands accused of raising funds through the unregistered offering of the Blazar Token, a crypto asset he created, which eventually collapsed in May 2022.
The SEC’s complaint further alleges misappropriation of investor funds, including diverting substantial amounts to his crypto asset wallets and using them for personal expenses, such as a bathroom renovation.
According to the SEC, DeSalvo managed to raise a minimum of $620,000 from around 220 investors between the launch of the Blazar Token in November 2021 and its subsequent collapse.
The complaint reveals that DeSalvo made “false claims” to investors, stating that the Blazar Token was registered with the SEC and that it would replace existing state pension systems. He further “deceived” investors by falsely assuring them that automatic payroll deductions would facilitate their investment and guarantee extraordinary returns.
Ultimately, DeSalvo allegedly misused and misappropriated the funds entrusted to him. Notably, the SEC’s complaint highlights DeSalvo’s deliberate targeting of fellow law enforcement and first responders in his fraudulent schemes.
In addition to the Blazar Token scheme, the SEC’s complaint also exposes an earlier fraud initiated by DeSalvo. Beginning in late January 2021, he allegedly solicited investors, primarily through social media, for an investment venture that involved trading stocks, options, and crypto asset securities.
Within weeks of raising $95,000 from 17 investors, DeSalvo reportedly lost a significant portion of the funds through speculative investments and misappropriated the rest. He proceeded to inform investors that poor market conditions led to the complete devaluation of the securities.
Gurbir S. Grewal, Director of the SEC’s Division of Enforcement, condemned DeSalvo’s actions, stating:
We allege that DeSalvo orchestrated several fraudulent investment schemes that targeted law enforcement personnel and promised astronomical returns, including one involving a crypto asset security that would somehow replace traditional state pension systems. Rather than producing any returns or revolutionary technology, he instead misappropriated and misused investor money.
Grewal further emphasized the breach of trust perpetrated by DeSalvo, who “exploited” his former position as a corrections officer to gain the confidence of fellow law enforcement professionals, many of whom invested their “hard-earned” savings with him.
The SEC’s complaint, filed in the U.S. District Court for the District of New Jersey, charges DeSalvo with violating antifraud and offering registration provisions of the securities laws. The SEC seeks injunctive relief, disgorgement of ill-gotten gains with prejudgment interest, and imposition of civil penalties.
Simultaneously, the U.S. Attorney’s Office for the District of New Jersey has announced criminal charges against DeSalvo, further underscoring the severity of the allegations and the commitment to holding him accountable for his actions.
At the time of writing, Bitcoin (BTC) maintains its upward trajectory in price, currently trading at $26,700, reflecting a notable increase of over 3% within the past 24 hours.
Featured image from iStock, chart from TradingView.com
Binance CEO, Changpeng ‘CZ’ Zhao has recently provided details on a failed $20 million scam attempt in a bid to keep the crypto community on alert for future occurrences.
In a tweet on August 2, Changpeng Zhao described a recent scam attempt as “clever,” stating that it was “luckily” prevented as the bad actors in the crypto space seem to have gotten better.
Related Reading: Curve DAO (CRV) Price Recovery Post-Exploit: What Would Be A Realistic Scenario?
Specifically, the Binance CEO drew attention to how these scammers now generate addresses with identical starting and ending letters as other wallet addresses.
Using these new addresses, they then proceed to impersonate other network participants and swindle unsuspecting crypto users. Technically, these kinds of scams are referred to as “zero-transfer phishing attacks.”
I want to share this (luckily) unsuccessful, but very clever and close scam incident from yesterday
. Saved $20m. Hope it may also save you one day.
The scammers are so good now they generate addresses with the same starting and ending letters, which is what most people check… https://t.co/DFpdX8aNay
— CZ
Binance (@cz_binance) August 2, 2023
Changpeng Zhao noted that these scams are particularly effective as most crypto users only confirm the first and last characters of an address when conducting transactions.
In fact, he stated that most wallet designs exclude the middle parts of addresses in an attempt to offer a better user interface to users
Asides from creating similar wallet addresses, the Binance CEO mentioned that these scammers would send “dust transactions” so they could be registered in their targets’ transaction history.
To explain, dust refers to a minute amount of cryptocurrency, usually valued at less than a cent, and cannot be traded on any exchange.
With the scammer’s address now present in their target’s transaction history, one can unknowingly transfer assets to these bad actors, especially if the impersonated address is one they constantly transact with.
Changpeng Zhao stated that a zero phishing attack happened to a veteran crypto operator on Aug 1 in which they transferred $20 million worth of USDT to the wrong address.
For context, the original wallet address was 0xa7Bf48749D2E4aA29e3209879956b9bAa9E90570, while the phishing address was 0xa7B4BAC8f0f9692e56750aEFB5f6cB5516E90570.
Luckily, the operator detected the scam quickly, and Binance was able to officially request for Tether to freeze the stolen USDT. The stablecoin operator responded promptly by blacklisting the wallet to prevent any further deposit or withdrawal.
Related Reading: Ethereum DeFi Coins Plunge As Curve Concerns Threaten Major Market Crash
The Binance CEO rounded off his tweet by stating that a fast reaction was vital to reclaiming users’ funds in these kinds of attacks. However, he did state that the assets recovery may take some time as the sender would have to complete a number of processes, including submitting a police report.
It is no news that the crypto space is riddled with heists, scams, and attacks which result in the loss of millions of dollars yearly. And these crypto scams are considered one of the major plagues in the crypto space.
According to data from Certik Security, crypto scams and hacks claimed over $313 million in just Q2 2023 alone. Another report from TRM Labs in June 2023 said that over $9 billion was lost to various scams and frauds in 2022. A huge portion (around $7.8 billion) of this figure was lost to Ponzi schemes alone, TRM added.
Featured image from Binance, chart from Tradingview